WTF is Mughthesec!?
› poking on a piece of undetected adware
8/08/2017
love these blog posts? support my tools & writing on patreon! Mahalo :)

Want to play along? I've shared the adware, which can be downloaded here (password: infect3d).
Background
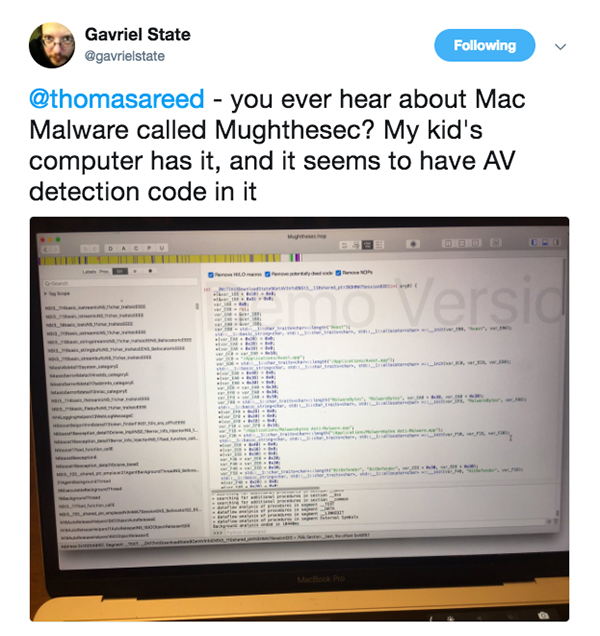
Yesterday Gavriel State (@gavrielstate) posted an interesting tweet:
Interestingly, googling "Mughthesec" only returned one relevant hit; a post on Apple's online's forums tilted "Safari does not render Gmail correctly". Posted on August 2nd, user 'giveen' stated that, "Only in Safari, when this specific user logins, it does not render Gmail correctly. Only Gmail. Only in Safari." Following another user's suggestion, 'giveen ' ran EtreCheck which noted several "unknown files:"
- ~/Library/LaunchAgents/com.Mughthesec.plist
- ~/Library/Application Support/com.Mughthesec/Mughthesec
As neither the sample, Mughthesec, nor the (signed!) installer were detected by any AV engines on Virus Total I decided to take a closer look.
Analysis
Let's start with the installer disk image. Uploaded to VirusTotal on August 4th as Player.dmg, it currently remains undetected:

Using WhatsYourSign, we can examine the signing info:
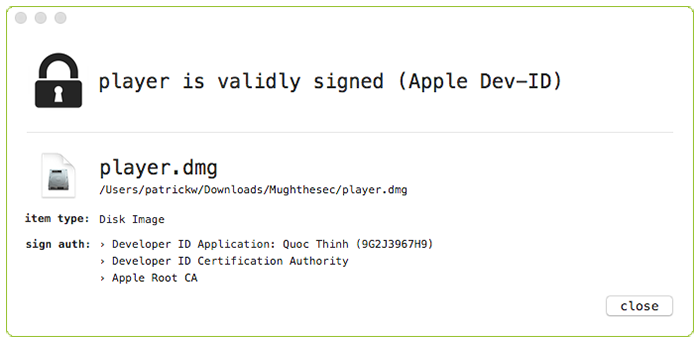
Using spctl, we can confirm the disk image's certificate is still valid (i.e. not rejected):
$ spctl -a -t install -vv ~/Downloads/Mughthesec/Player.dmg
~/Downloads/Mughthesec/player.dmg: accepted
source=Developer ID
origin=Developer ID Application: Quoc Thinh (9G2J3967H9)
~/Downloads/Mughthesec/player.dmg: accepted
source=Developer ID
origin=Developer ID Application: Quoc Thinh (9G2J3967H9)
Double-clicking the disk image, Player.dmg mounts it, revealing a single file Installer.app:
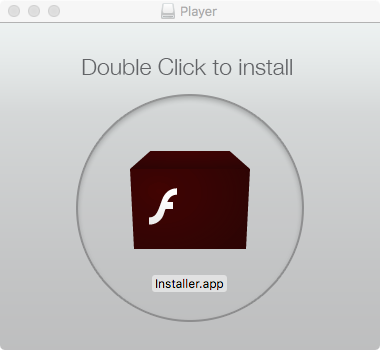
Besides it's icon and name, the Installer.app's' Info.plist file, shows it masquerading as Flash installer:
cat Installer.app/Contents/Info.plist
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
...
<key>CFBundleIdentifier</key>
<string>com.FlashPlayer</string>
<key>CFBundleName</key>
<string>FlashPlayerInstaller</string>
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
...
<key>CFBundleIdentifier</key>
<string>com.FlashPlayer</string>
<key>CFBundleName</key>
<string>FlashPlayerInstaller</string>
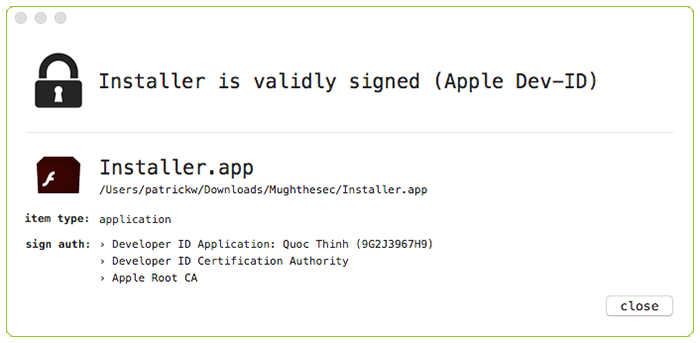
This application, is also signed with the same Apple Developer ID:
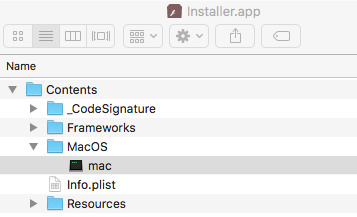
Examining its application bundle, we can see its executable is a binary name 'mac' ... how creative!
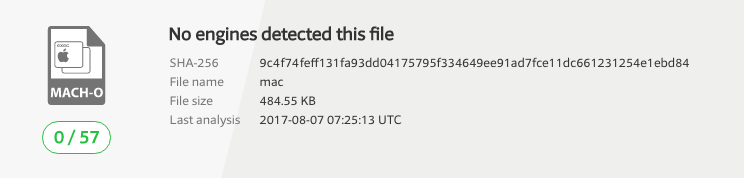
This binary is also (currently) undetected by any AV engine on Virus Total:
Taking a quick peak at the installer binary shows what appears to be anti-anti-virus logic:
We can also run strings to search for embedded URLs:
$ strings -a ~/Downloads/Mughthesec/Installer.app/Contents/MacOS/mac | grep http
http://api.simplyeapps.com/p
http://cdn.simplyeapps.com/screens/precheck/DmFybQ==
http://cdn.simplyeapps.com/screens/progress/DmFybQ==
http://cdn.simplyeapps.com/screens/complete/DmFybQ==
http://api.simplyeapps.com/l
http://api.simplyeapps.com/p
http://cdn.simplyeapps.com/screens/precheck/DmFybQ==
http://cdn.simplyeapps.com/screens/progress/DmFybQ==
http://cdn.simplyeapps.com/screens/complete/DmFybQ==
http://api.simplyeapps.com/l
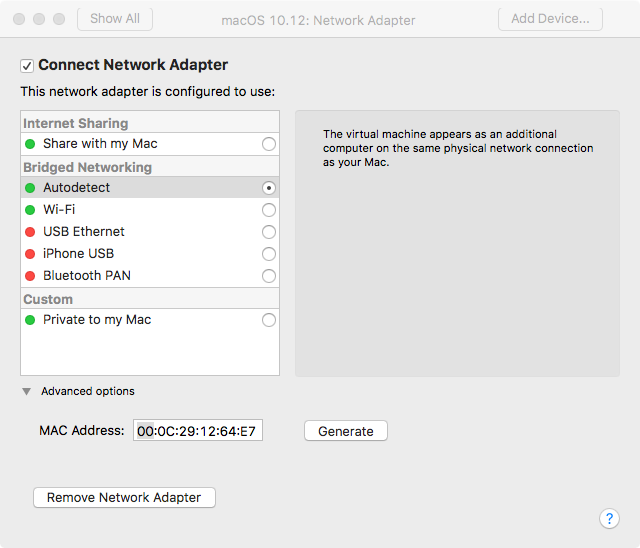
Now, before we run this in a VM - let's change the MAC address of the virtual machine. This is required step, because it turns out that the installer actually doesn't do anything malicious, (besides actually installing a legit copy of Flash), if it detects it running in VM. Thomas Reed (@thomasareed) correctly guessed that this 'VM detection' is done by examining the MAC address (VMWare VMs have 'recognizable' MAC address). Apparently this is common trick used in macOS adware!
To change the VM's mac address, shut it down, then change it via the VM's Network Adapter's settings (click 'Advanced Options' to modify the MAC address).
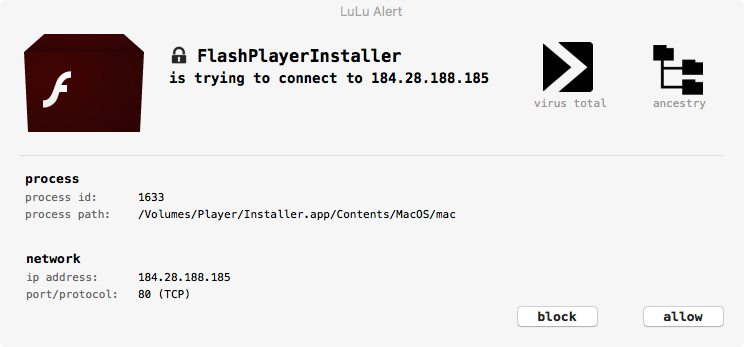
Alright, let's run the damn Installer.app already! First thing, LuLu (my soon-to-be-released macOS firewall!) detects an outgoing network connection:
Once the outgoing connection is allowed, the Installer application kindly asks the user to install some 'adware' and potentially unwanted programs:
- Advanced Mac Cleaner
- Safe Finder
- Booking.com
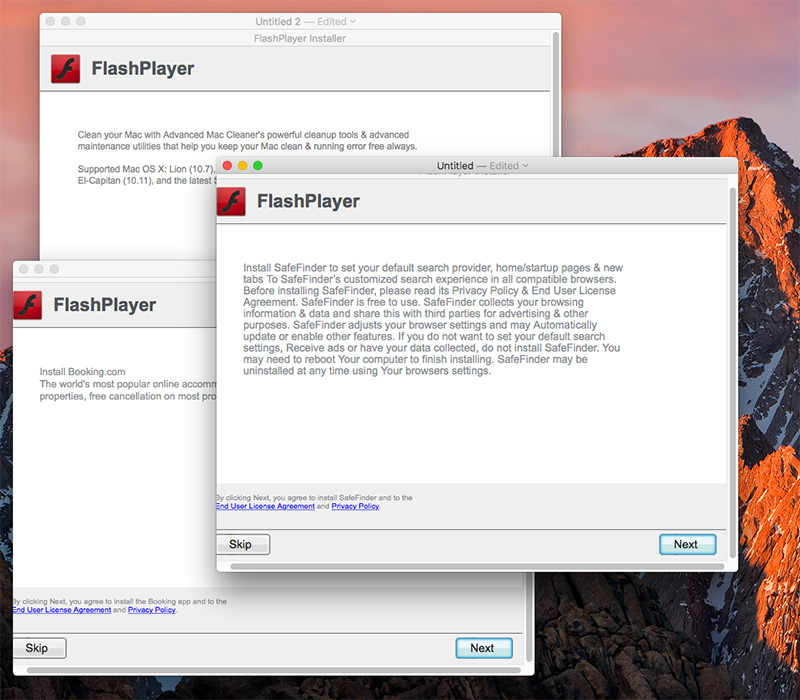
Since we're playing along, we click 'Next' to install it all!
Not too unexpectedly, the Advanced Mac Cleaner triggers a few BlockBlock warnings as it attempts to install a persistent launch agent and login item:
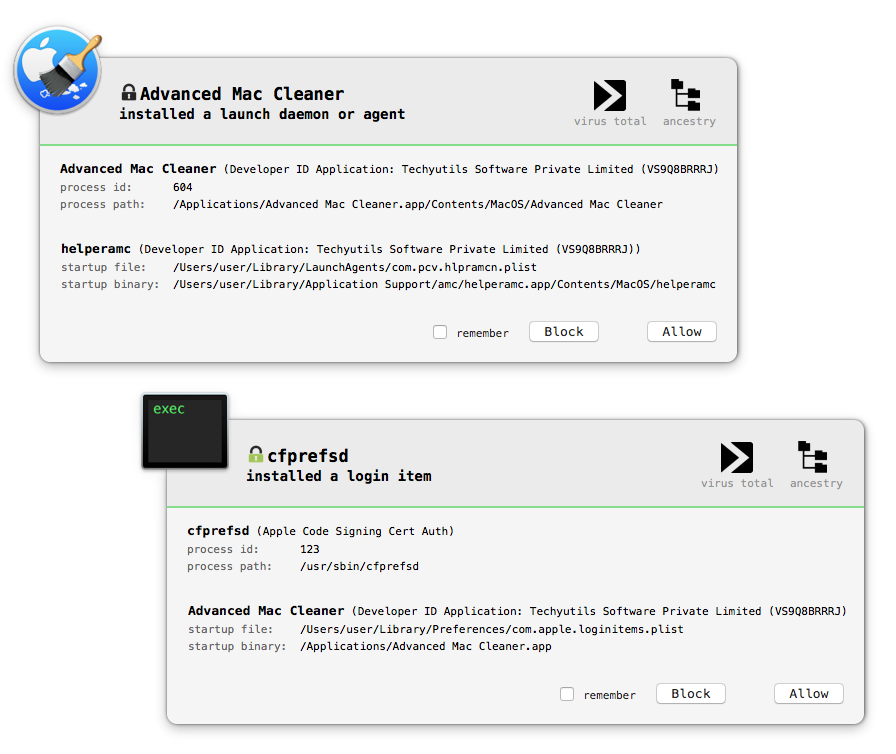
It also kindly informs us of several 'critical' issues. How thoughtful :P
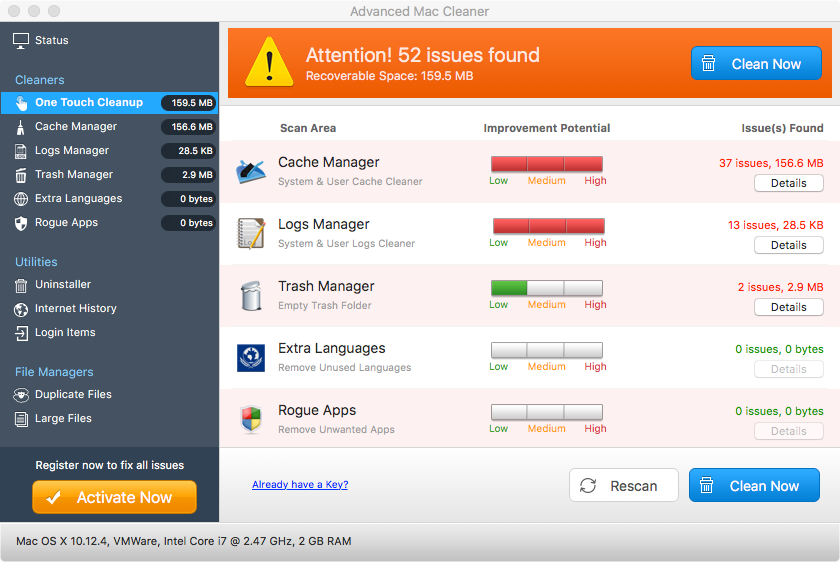
Moving on to 'Safe Finder', BlockBlock as alerts us of a process named 'i' persisting something named 'Mughthesec as a launch agent.
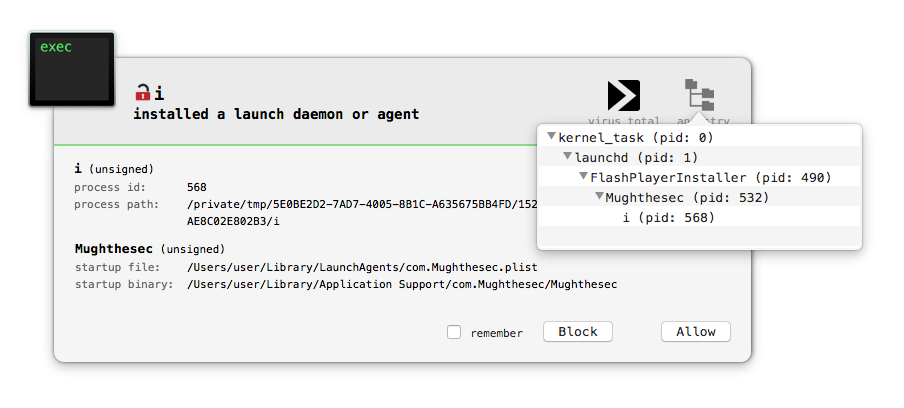
An open-source process monitoring utility I wrote (based on the Proc Info library) shows Mughthesec being started by the Installer application (FlashPlayerInstaller, pid: 490):
# procMonitor
process start:
pid: 532
path: /private/tmp/F3A53281-D3FA-4F32-B996-3EE0FCF522D5/62/Mughthesec
user: 501
args: (
"/tmp/F3A53281-D3FA-4F32-B996-3EE0FCF522D5/62/Mughthesec",
2,
na,
na,
"F3A53281-D3FA-4F32-B996-3EE0FCF522D5"
)
ancestors: (
490,
1
)
binary:
name: Mughthesec
path: /private/tmp/F3A53281-D3FA-4F32-B996-3EE0FCF522D5/62/Mughthesec
signing info: {
signatureStatus = "-67062";
} (isApple: 0 / isAppStore: 0)
process start:
pid: 532
path: /private/tmp/F3A53281-D3FA-4F32-B996-3EE0FCF522D5/62/Mughthesec
user: 501
args: (
"/tmp/F3A53281-D3FA-4F32-B996-3EE0FCF522D5/62/Mughthesec",
2,
na,
na,
"F3A53281-D3FA-4F32-B996-3EE0FCF522D5"
)
ancestors: (
490,
1
)
binary:
name: Mughthesec
path: /private/tmp/F3A53281-D3FA-4F32-B996-3EE0FCF522D5/62/Mughthesec
signing info: {
signatureStatus = "-67062";
} (isApple: 0 / isAppStore: 0)
The process monitor also shows this process (Mughthesec, pid: 532), spawning executing the 'i' process out of /tmp:
# procMonitor
process start:
pid: 568
path: /private/tmp/5E0BE2D2-7AD7-4005-8B1C-A635675BB4FD/15261EBB-ED0B-46DA-8C3B-AE8C02E802B3/i
user: 501
args: (
"/tmp/5E0BE2D2-7AD7-4005-8B1C-A635675BB4FD/15261EBB-ED0B-46DA-8C3B-AE8C02E802B3/i",
"5E0BE2D2-7AD7-4005-8B1C-A635675BB4FD",
"S+wIS+tmwyirlkak8AAF36JIq8TSRdg...==",
10
)
ancestors: (
532,
490,
1
)
binary:
name: i
path: /private/tmp/5E0BE2D2-7AD7-4005-8B1C-A635675BB4FD/15261EBB-ED0B-46DA-8C3B-AE8C02E802B3/i
signing info: {
signatureStatus = "-67062";
} (isApple: 0 / isAppStore: 0)
process start:
pid: 568
path: /private/tmp/5E0BE2D2-7AD7-4005-8B1C-A635675BB4FD/15261EBB-ED0B-46DA-8C3B-AE8C02E802B3/i
user: 501
args: (
"/tmp/5E0BE2D2-7AD7-4005-8B1C-A635675BB4FD/15261EBB-ED0B-46DA-8C3B-AE8C02E802B3/i",
"5E0BE2D2-7AD7-4005-8B1C-A635675BB4FD",
"S+wIS+tmwyirlkak8AAF36JIq8TSRdg...==",
10
)
ancestors: (
532,
490,
1
)
binary:
name: i
path: /private/tmp/5E0BE2D2-7AD7-4005-8B1C-A635675BB4FD/15261EBB-ED0B-46DA-8C3B-AE8C02E802B3/i
signing info: {
signatureStatus = "-67062";
} (isApple: 0 / isAppStore: 0)
This 'i' process is what persists and starts 'launch agent' instance of Mughthesec. We can see this, again, via the process monitor which shows process 'i' (pid: 568) invoking launchctl with the 'load' command line option and the path to the launch agent plist:
# procMonitor
process start:
pid: 576
path: /bin/launchctl
user: 501
args: (
"/bin/launchctl",
load,
"/Users/user/Library/LaunchAgents/com.Mughthesec.plist"
)
ancestors: (
568,
532,
490,
1
)
binary: name: launchctl
path: /bin/launchctl
signing info: {
signatureStatus = 0;
signedByApple = 1;
signingAuthorities = (
"Software Signing",
"Apple Code Signing Certification Authority",
"Apple Root CA"
);
} (isApple: 1 / isAppStore: 0)
process start:
pid: 576
path: /bin/launchctl
user: 501
args: (
"/bin/launchctl",
load,
"/Users/user/Library/LaunchAgents/com.Mughthesec.plist"
)
ancestors: (
568,
532,
490,
1
)
binary: name: launchctl
path: /bin/launchctl
signing info: {
signatureStatus = 0;
signedByApple = 1;
signingAuthorities = (
"Software Signing",
"Apple Code Signing Certification Authority",
"Apple Root CA"
);
} (isApple: 1 / isAppStore: 0)
Ok, so let's take a closer look at the Mughthesec launch agent and binary. The Mughthesec launch agent plist is located at ~/Library/LaunchAgents/com.Mughthesec.plist:
$ cat ~/Library/LaunchAgents/com.Mughthesec.plist
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>Label</key>
<string>com.Mughthesec</string>
<key>ProgramArguments</key>
<array>
<string>/Users/user/Library/Application Support/com.Mughthesec/Mughthesec</string>
<string>r</string>
</array>
<key>RunAtLoad</key>
<true />
<key>StartInterval</key>
<integer>14400</integer>
</dict>
</plist>
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>Label</key>
<string>com.Mughthesec</string>
<key>ProgramArguments</key>
<array>
<string>/Users/user/Library/Application Support/com.Mughthesec/Mughthesec</string>
<string>r</string>
</array>
<key>RunAtLoad</key>
<true />
<key>StartInterval</key>
<integer>14400</integer>
</dict>
</plist>
From this plist we can see that the launch agent will:
- execute a binary: ~/Library/Application Support/com.Mughthesec/Mughthesec
- pass in a parameter: 'r'
- be automatically started whenever the user logs in, as 'RunAtLoad' is set to true
The 'Mughthesec' binary, ~/Library/Application Support/com.Mughthesec/Mughthesec, is unsigned:
$ codesign -dvvv "~/Library/Application Support/com.Mughthesec/Mughthesec"
~/Library/Application Support/com.Mughthesec/Mughthesec: code object is not signed at all
~/Library/Application Support/com.Mughthesec/Mughthesec: code object is not signed at all
It is also (currently) undetected by any AV engines on VirusTotal:

Running strings shows some embedded URLs:
$ strings -a ~/Library/Application Support/com.Mughthesec/Mughthesec | grep http
http://api.mughthesec.com/ai
http://api.mughthesec.com/l
http://api.mughthesec.com/ai
http://api.mughthesec.com/l
Attempting to access those URLs in a browser, appears to result in an error:
However, the host mughthesec.com does appear to be online, resolving to 192.64.119.107:
$ nslookup mughthesec.com
Non-authoritative answer:
Name: mughthesec.com
Address: 192.64.119.107
Non-authoritative answer:
Name: mughthesec.com
Address: 192.64.119.107
This IP address, 192.64.119.107, appears to be rather malicious:
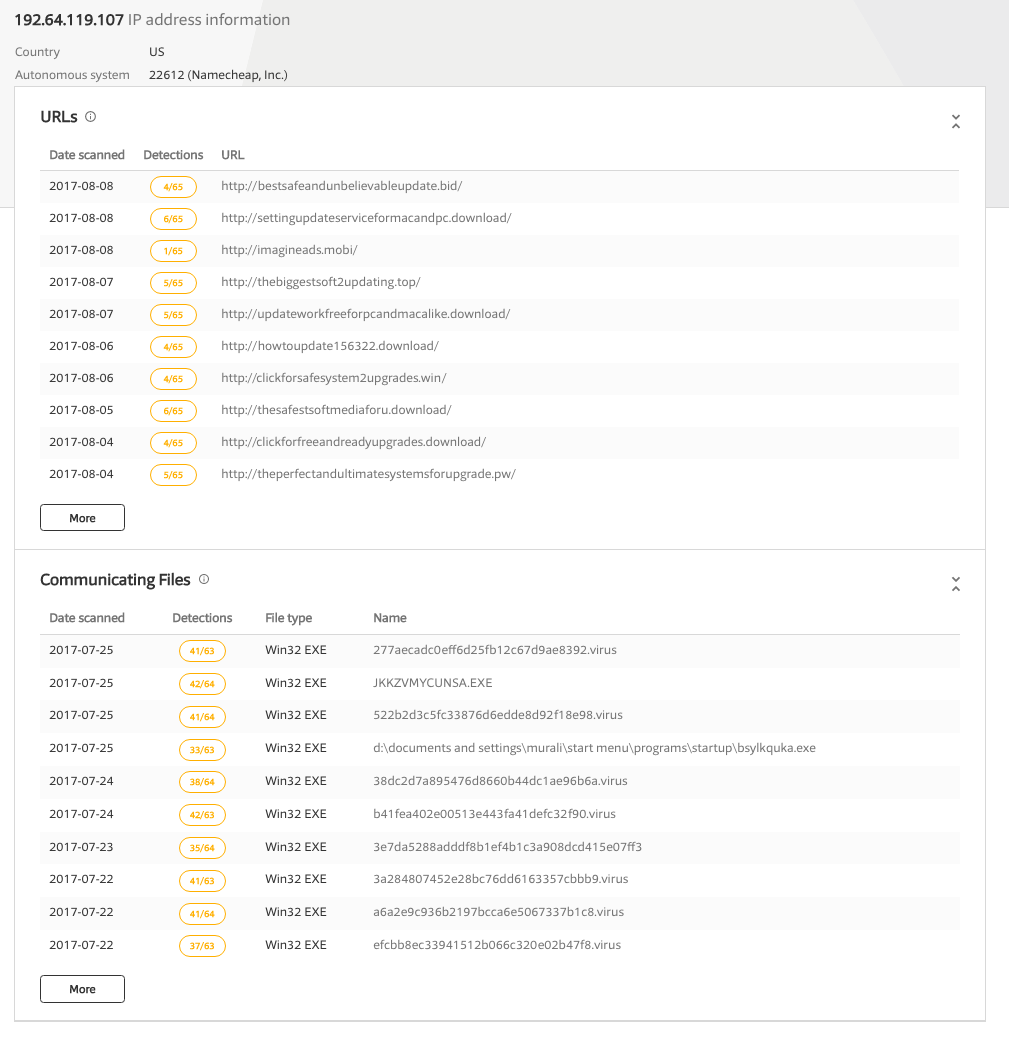
So what does the Mughthesec binary actually do? Lets take a peek! However, I want to point out that I've learned (the hard way) that spending a large amount of time reversing adware can quickly drive one somewhat mad...so here, we'll only perform a cursory look.
A common tactic of adware is to hijack the victims browser (homepage, inject ads, etc) for financial gain. Mughthesec (which is installed when the user "agrees" to install "Safe Finder") appears to conform to goal. Specifically we can see that Safari's home page has been set to http://default27061330-a.akamaihd.net/s?q=@@@&_pg=564D4420-C090-470B-9C13-6760B31264E7
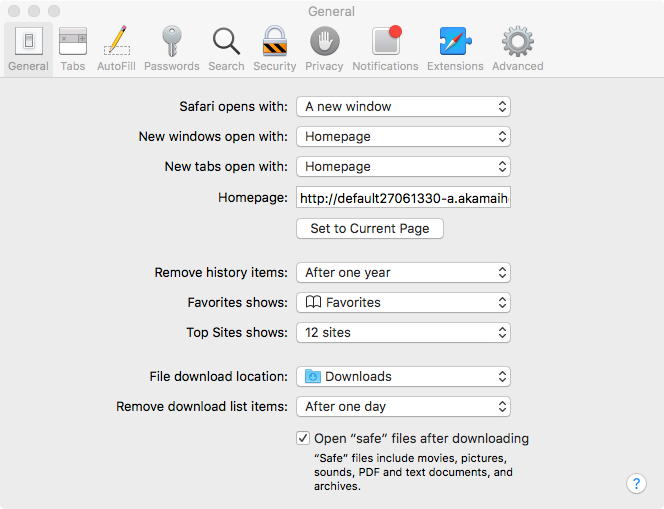
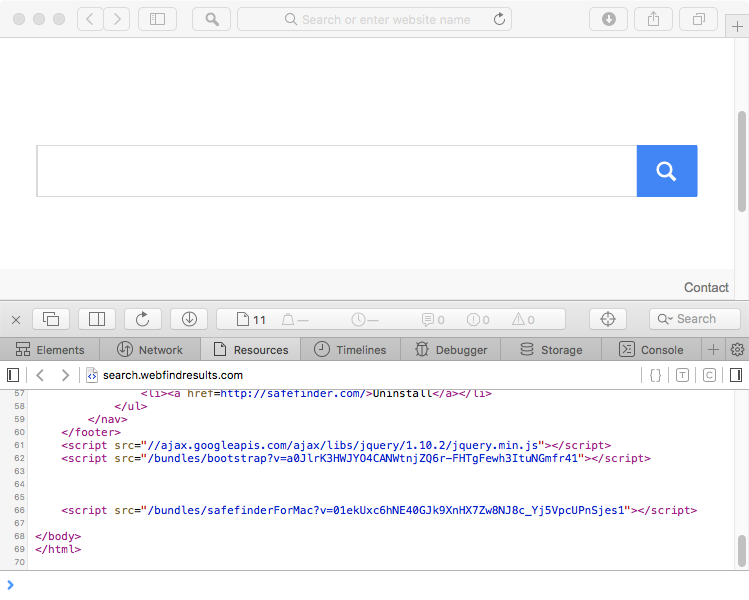
If we open Safari; indeed the home page has been hijacked - though in a seemingly innocuous way. It simply displays a rather 'clean' search page - though looking at the source, we can the inclusion of several scripts 'Safe Finder' scripts:
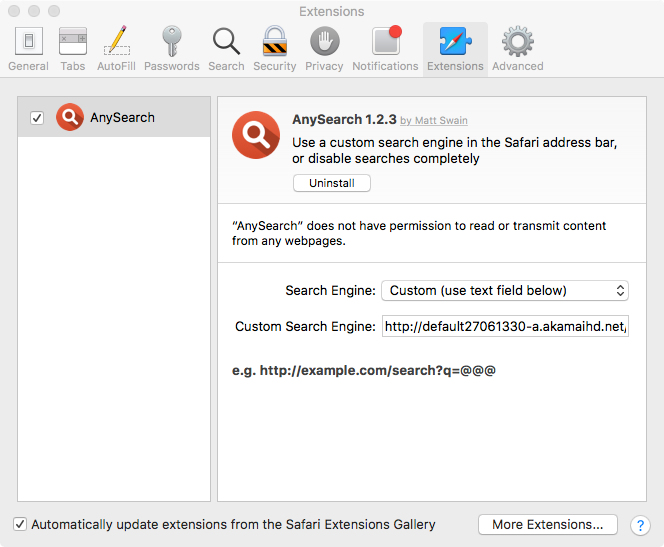
Also, examining the installed extensions we can see that an "Any Search" browser extension was installed:
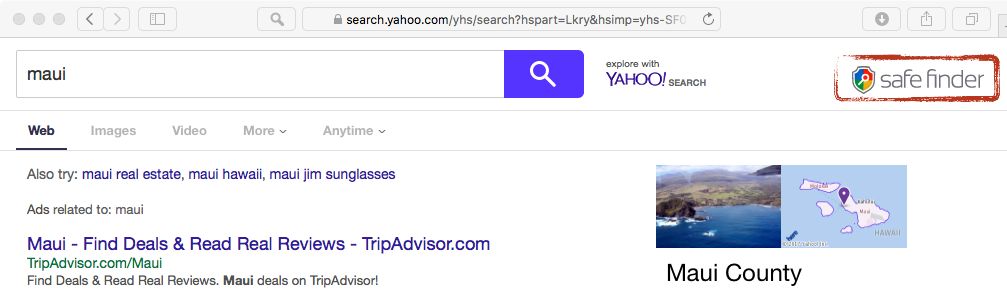
Searches are funneled thru various affiliates, before ending up being serviced by Yahoo Search. However, 'Safe Finder' logic (such as an icon, and likely other scripts) are injected into all search results:
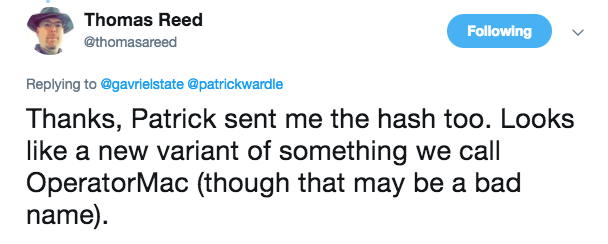
At this point, I'm calling it a night! It appears that Mughthesec is simply some 'run-of-the-mill' macOS malware. But is it new? Not likely. According to the mac adware analysis guru, Thomas Reed; this "looks like a new variant of something we call OperatorMac":
Moreover, @noarfromspace pointed me towards several samples from earlier this year (spring?) that appear to be related:
Conclusion
In the blog post, we sought to answer the question, "What is Mughthesec?" The answer; likely a new variant of the 'SafeFinder/OperatorMac' adware. Yes it's rather unsophisticated macOS malware, but it's installer is signed (to 'bypass' Gatekeeper) and at the time of this analysis no anti-virus engines were detected it....and mac users are being infected :|
Speaking of infection, due to the fact that the installer is masquerading as Flash Player installer, it's likely that this adware is relying on common infection techniques to gain new victims. If I had to guess its infection vector is likely one (or all?) of the following:
- fake popups on 'shady' websites
- malicious ads, perhaps on legit websites
In terms of detection, we showed how BlockBlock will alert when the adware goes to persist. Neat!
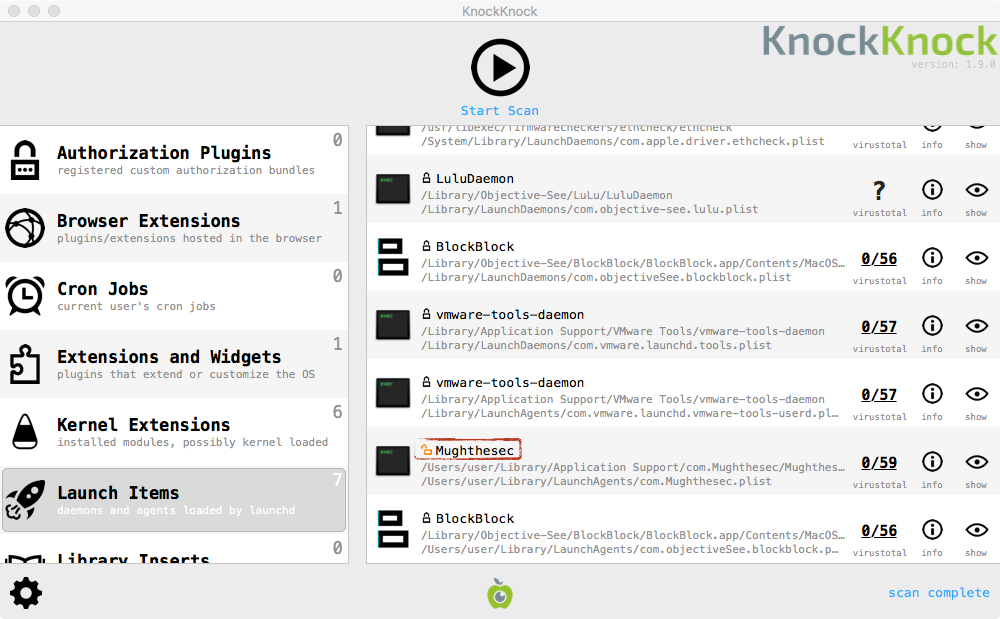
KnockKnock can also be used to (after the fact), to reveal infections. For example, it can reveal the presence of the unsigned launch agent:
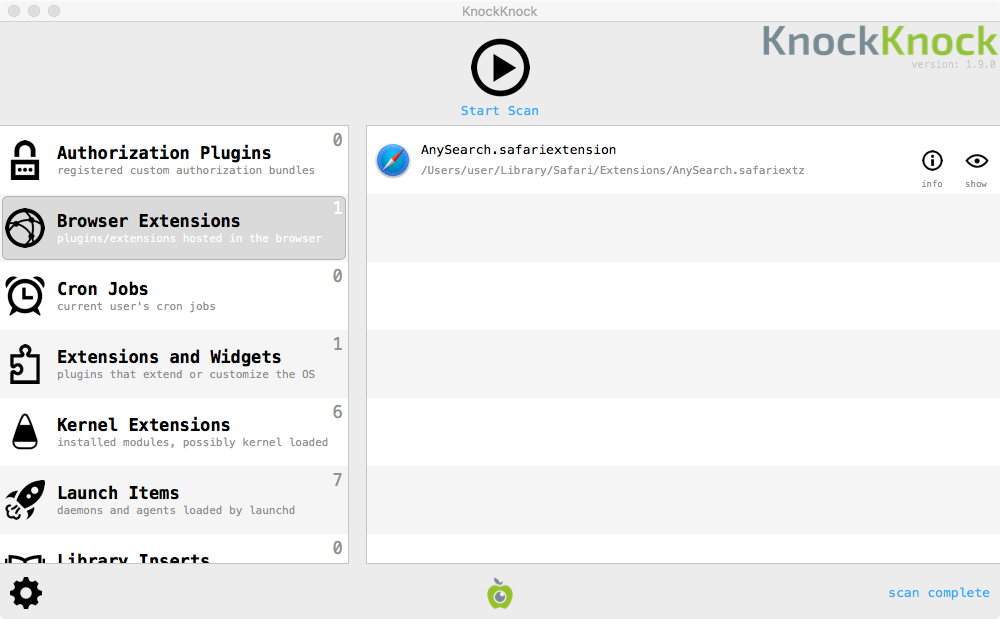
And what about the malicious browser extension? Yup, KnockKnock can show that too:
Hooray! Objective-See FTW ❤️
To manually disinfect Mughthesec:
- unload the launch agent via: launchctl unload ~/Library/LaunchAgents/com.Mughthesec.plist
- delete ~/Library/Application Support/com.Mughthesec/Mughthesec
- delete ~/Library/LaunchAgents/com.Mughthesec.plist
- delete the 'Any Search' browser extension
love these blog posts & tools? you can support them via patreon! Mahalo :)