A Surreptitious Cryptocurrency Miner in the Mac App Store?
› a free calender app possesses more than meets the eye!
03/11/2018
love these blog posts? support my tools & writing on patreon :)

Want to play along? I've shared the application, which can be downloaded here.
Background
Hooray it's Sunday, the "day of rest", right? Well, if you're a CPU-hungry cryptocurrency miner you never take a day off. And if you're a macOS security researcher, well, no days off either!
Earlier today Dan Goodin from Ars Technica pinged me about an application on the official Mac App Store that reportedly was rather surreptitiously mining cryptocurrency. I was intrigued, and thus decided to investigate!
Analyzing 'Calendar 2'
The application in question, is innocuously named Calendar 2 by a company named Qbix. Currently it is still available on official Mac App Store at itunes.apple.com/us/app/calendar-2/id415181149
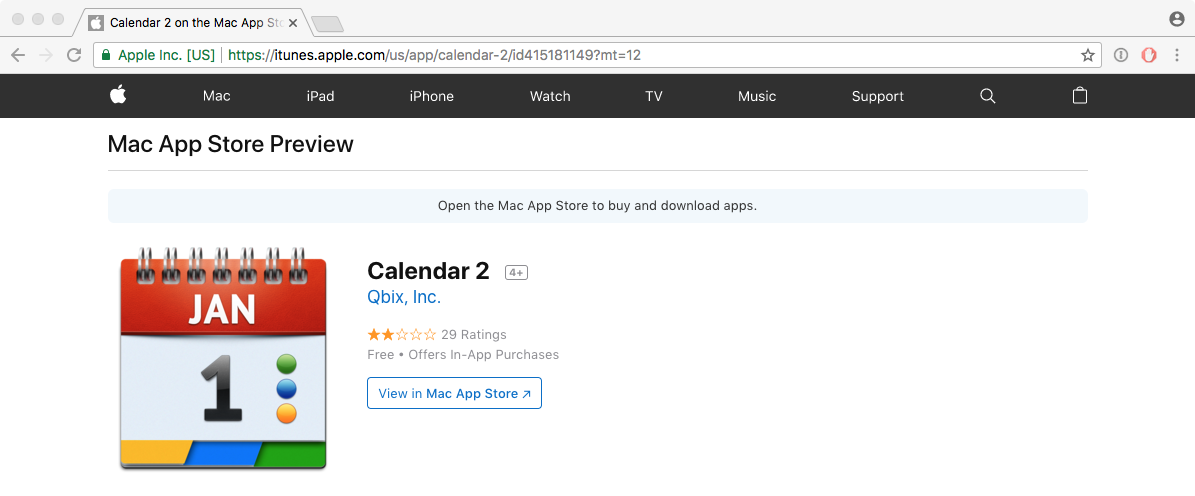
update: after reporting this to Apple, the application has been removed from the Mac App Store!
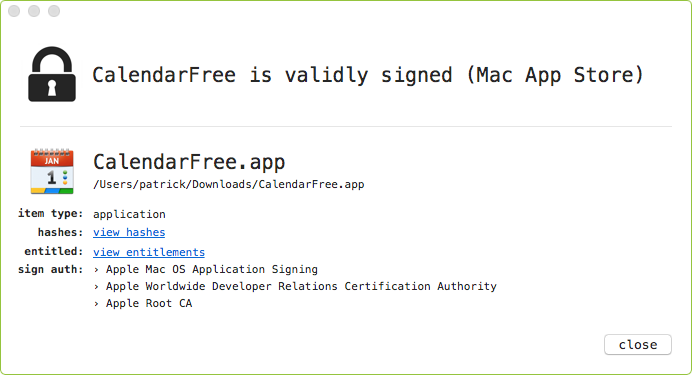
Using macOS's "App Store", we can install the application (note: its application bundle is named CalendarFree.app). And yes, as is the case with all apps in the official Mac App Store, it's validly signed:
Running strings on the Application's binary (CalendarFree.app/Contents/MacOS/CalendarFree) reveals it contains various strings that appear to be related to mining cryptocurrency:
$ strings -a ~/Downloads/CalendarFree.app/Contents/MacOS/CalendarFree ... MinerManager updateMiner _parseMinerSetting com.qbix.MineroMode Miner: Start. core %d; cpuLimit %d; port %d; slowMemory %@; currency: %@; token: %@ Miner: Stopped Miner: Check: hashrate %d; status: %d
Dumping the Objective-C class information via jtool, we see classes such as MinerManager:
$ ./jtool -d objc -v CalendarFree.app/Contents/MacOS/CalendarFre
@interface MinerManager : ? // 13 properties: @property (nonatomic) long long currentPortIndex; @property (copy) NSString slowMemoryMode; @property (nonatomic) long long cpuLimit; @property (nonatomic) long long coreLimit; @property (copy) NSString token; @property (copy) NSString algorythm; ... // 32 instance methods /* 0 - 0x100092e50 */ - runMiningPingReport; /* 1 - 0x100092f10 */ - checkModeSelected; /* 2 - 0x100077db0 */ - init; /* 3 - 0x100077e10 */ - updateToReflectUserMode; /* 4 - 0x100077e30 */ - updateMiner; /* 5 - 0x100077fc0 */ - runMining; /* 6 - 0x1000780d0 */ - stopMining; /* 7 - 0x100078130 */ - checkMiningStatus; /* 8 - 0x100078200 */ - startMiningCheckLoop; /* 9 - 0x100078260 */ - stopMiningCheckLoop; ... @end
Finally using MachOView, we see the application is linked against what appears to be a cryptocurrency mining framework: Coinstash_XMRSTAK.framework
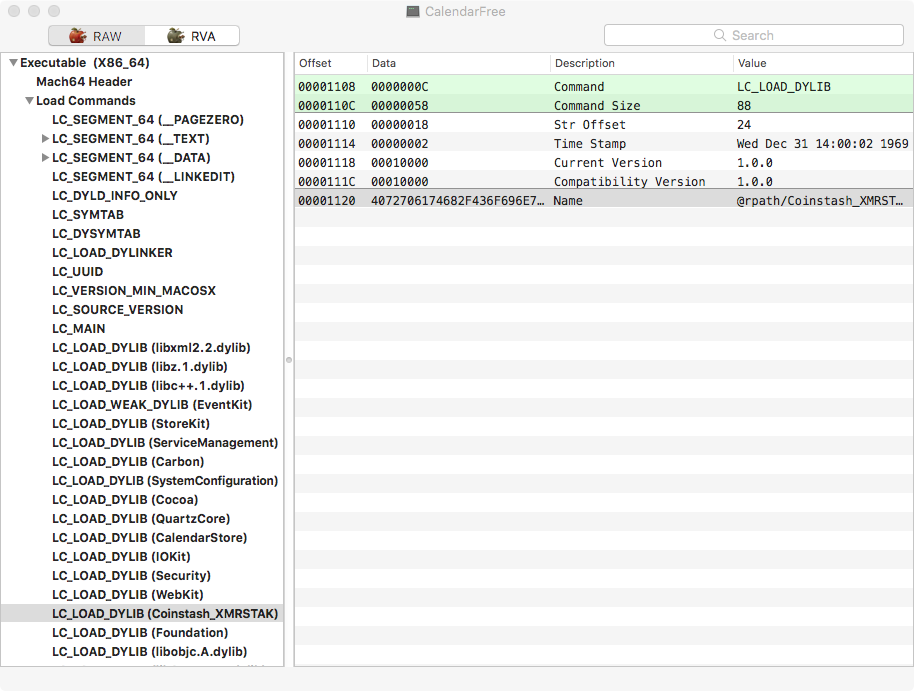
Ok, so it's pretty clear that, although Apple claims to thoroughly vet all applications submitted to the Mac App Store, the Calendar 2 application possesses "hidden" cryptocurrency mining capabilities! Let's now take a closer look at exactly how it may take over your CPU to mine monero (XMR).
Generally speaking, application logic begins in the applicationDidFinishLaunching: delegate method. Decompiling this method, we see block invoked that executes several MinerManager methods:
void -[CalendarController applicationDidFinishLaunching:]
{
...
dispatch_after(dispatch_time(0x0, 0x3b9aca00), *__dispatch_main_q, ^ {
/* block implemented _52-[CalendarController applicationDidFinishLaunching:]_block_invoke */
});
}
void _52-[CalendarController applicationDidFinishLaunching:]_block_invoke(void * _block) {
...
[[MinerManager manager] runMiningPingReport];
[[MinerManager manager] updateMiner];
return;
}
The call to [MinerManager manager] will triggers a one time allocation and initialization of a MinerManager object. As part of this initialization it calls the runMining method:
$ lldb /Applications/CalendarFree.app/
Current executable set to '/Applications/CalendarFree.app/' (x86_64).
(lldb) b -[MinerManager runMining]
Breakpoint 1: where = CalendarFree`-[MinerManager runMining]
...
Process 2944 stopped
* thread #1, queue = 'com.apple.main-thread', stop reason = breakpoint 6.1
CalendarFree`-[MinerManager runMining]:
(lldb) bt
* frame #0: 0x0000000100077fc0 CalendarFree`-[MinerManager runMining]
frame #1: 0x0000000100077dff CalendarFree`-[MinerManager init] + 79
...
frame #5: 0x0000000100077d22 CalendarFree`+[MinerManager manager] + 98
By examining the decompilation of the runMining method, we can see it calling into the Coinstash_XMRSTAK framework:
void -[MinerManager runMining] {
rdx = self->_coreLimit;
r14 = [self calculateWorkingCores:rdx];
[_TtC17Coinstash_XMRSTAK9Coinstash setCPULimit:self->_cpuLimit];
r15 = [self getPort];
r12 = [self algorythm];
[self getSlotMemoryMode];
[_TtC17Coinstash_XMRSTAK9Coinstash startMiningWithPort:r15 password:self->_token
coreCount:r14 slowMemory:self->_slowMemoryMode currency:r12];
NSLog(@"Miner: Start. core %d; cpuLimit %d; port %d; slowMemory %@; currency: %@;
token: %@", r14, self->_cpuLimit, r15, self->_slowMemoryMode, r12, self->_token);
[self startMiningCheckLoop];
return;
}
As the framework is written in Swift (🤮), the method name is mangled. It's demangled name is:
+[Coinstash_XMRSTAK.Coinstash startMiningWithPort:password:coreCount:slowMemory:currency:].
Setting a breakpoint on this method, we can dump the arguments passed in:
$ lldb /Applications/CalendarFree.app/ ... Process 1811 stopped stop reason = breakpoint 1.1 +[Coinstash_XMRSTAK.Coinstash startMiningWithPort:password:coreCount:slowMemory:currency:] (lldb) po $rdi Coinstash_XMRSTAK.Coinstash (lldb) x/s $rsi 0x1000f1576: "startMiningWithPort:password:coreCount:slowMemory:currency:" (lldb) po $rdx 7777 (lldb) po $rcx qbix:greg@qbix.com
As reversing Swift is annoying and this blog post already has enough snippets of decompiled code, let's just allow the debugger execute over +[Coinstash_XMRSTAK.Coinstash startMiningWithPort ...] method, while watching (externally) process events via my ProcInfo process monitor:
# ./procInfo
[NEW EVENT: PROCESS START ('xmr-stak')]
pid: 1899
path: /Applications/CalendarFree.app/Contents/Frameworks/Coinstash_XMRSTAK.framework/
Versions/A/Resources/xmr-stak
args: (
"/Applications/CalendarFree.app/Contents/Frameworks/Coinstash_XMRSTAK.framework
/Resources/xmr-stak",
"--currency",
monero,
"-o",
"pool.graft.hashvault.pro:7777",
"-u",
G81Jc3KHStAWJjjBGzZKCvEnwCeRZrHkrUKji9NSDLtJ6Evhhj43DYP7dMrYczz5KYj...,
"-p",
"qbix:greg@qbix.com",
"--config",
"/var/folders/qm/mxjk9mls58d9ycd5c1vjt9w40000gn/T/com.qbix.Calendar/
com.beachio.coinstash/config.txt",
"--cpu",
"/var/folders/qm/mxjk9mls58d9ycd5c1vjt9w40000gn/T/com.qbix.Calendar/
com.beachio.coinstash/cpu.txt",
"--amd",
"/var/folders/qm/mxjk9mls58d9ycd5c1vjt9w40000gn/T/com.qbix.Calendar/
com.beachio.coinstash/amd.txt",
...
)
Ah, so there's the miner: xmr-stak! From its commandline arguments, it's clear to see it's mining monero (XMR), for a certain greg@qbix.com. Googling xmr-stak takes us to Coinsta.sh which provides services to "invest your spare cpu into cryptocurrency" 🙄
A posting in their forum provides more information about their "new crypto-miner app for macOS" named, xmr-stak. And if we download their free "Coinstash app", it contains the 'same' xmr-stak binary:
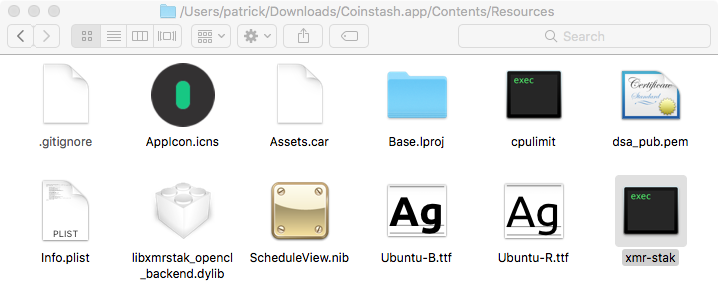
Ok back to our VM....looks like it's been mining away:
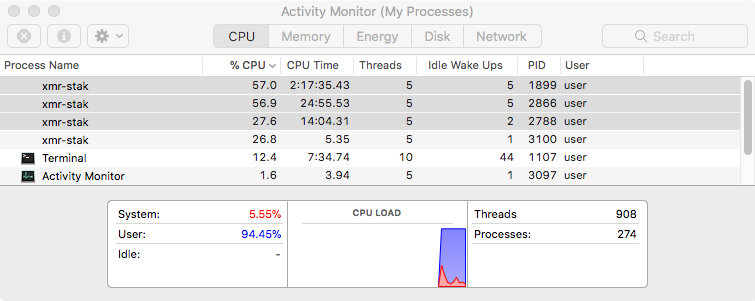
Might be wondering exactly what it's been doing? Lucky for us the 'Calendar' invokes the runMiningPingReport method to generates a report about mining operations, sending them off to calendar.qbix.com/api/mining.
Setting a breakpoint on the -[GTMHTTPFetcher initWithRequest:] method allows us to view this report data that's about to be uploaded:
$ lldb /Applications/CalendarFree.app/
Current executable set to '/Applications/CalendarFree.app/' (x86_64).
(lldb) b -[GTMHTTPFetcher initWithRequest:]
Breakpoint 1: where = CalendarFree`-[GTMHTTPFetcher initWithRequest:]
Process 2825 stopped
* thread #17, queue = 'com.apple.root.default-qos', stop reason = breakpoint 1.1
CalendarFree`-[GTMHTTPFetcher initWithRequest:]:
(lldb) po $rdx
<NSMutableURLRequest: 0x1018f04e0> { URL: https://calendar.qbix.com/api/mining }
(lldb) po [0x1018f04e0 HTTPBody]
{
"m_mode": true,
"a_l": false,
"u_mode": 3,
"language": "en-US",
"u_p": 0,
"mining": {
"statistic": {
"ZeroCounter": 0,
"AverageHashRate": 0.92911845445632935,
"CounterTime": 30,
"NonZeroCounter": 14,
"MaxHashRate": 21,
"MinHashRate": 10
},
"params": {
"Token": "qbix:greg@qbix.com",
"Algorithm": "graft",
"CPULimit": 25,
"EnableMiningMode": true,
"CPUBatteryLimit": 10,
"CoreLimit": 25,
"Ports": {
"7777": 1000000,
"5555": 160,
"3333": 40
}
}
},
"sv": "10.13.3",
"m_a_mode": false,
"la": false,
"t": "000c2909108f",
"tz_offset": -25200,
"u": 0,
"bv": "2.6.1",
"id": "2018-03-12 01:02:20 +0000",
"battery": {
"BatteryPlugIn": 111,
"TimeInterval": 60,
"BatteryCounters": 111
},
"l": "-1037.3,-122.0",
"tz_name": "PDT",
"u_s": 1,
"client_time": 1520827483,
...
}
Neat!
Before we wrap this up there's an interesting observation to make. As noted by the sharp-eyed @dogcow, the "Calendar 2" application actually tells us that it may utilize the spare cycles of our CPUs to perform cryptocurrency mining in the background:
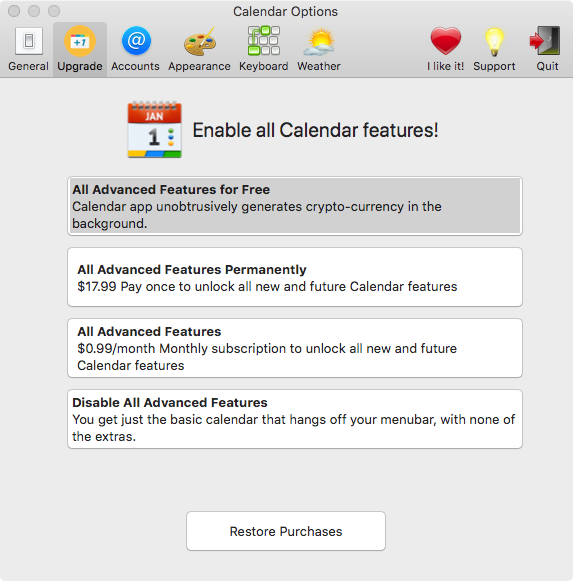
Hooray for honestly I guess!? And is getting "all advanced features for free" in return for allowing the app to turn your box into a cryptocurrency miner a fair deal? Maybe? But users clearly are *not* stoked about this:
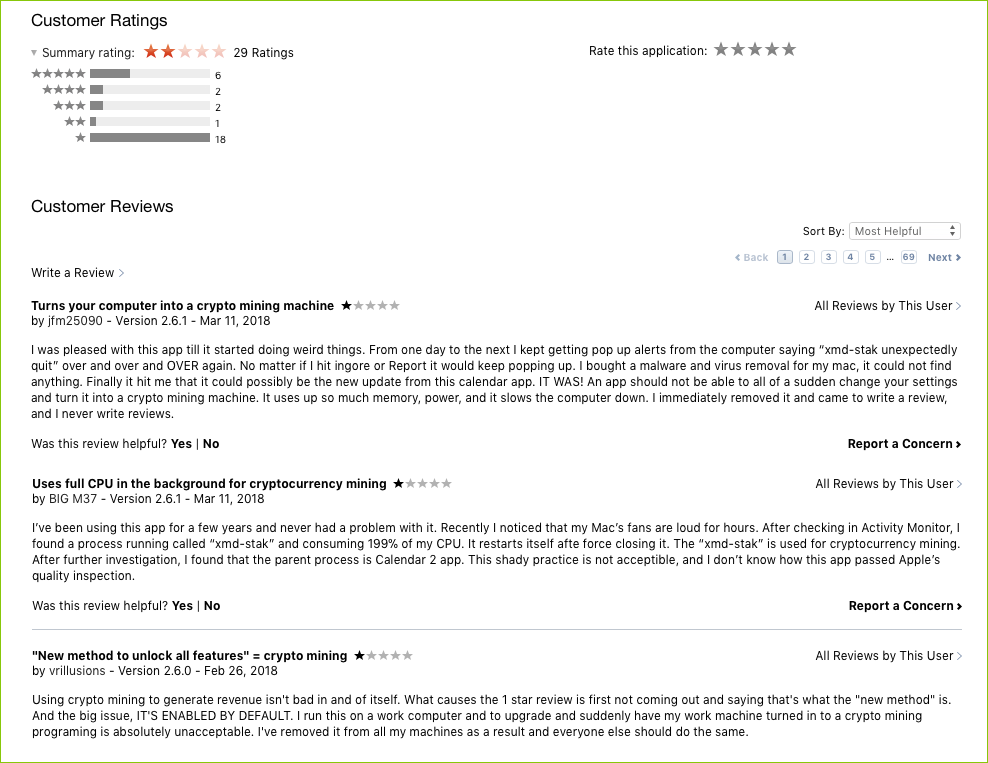
And what will Apple think about all this? I can't imagine they'll be happy with this behavior - even if it's (semi)documented within the application. I'm guessing even if this does not violate their stringent Mac App Store "Terms of Service" they'll likely side with the upset Mac users...but who knows.
Conclusions
In this blog post we analyzed an application, "Calendar 2", found on the official Mac App Store. Somewhat surprisingly it has the ability to rather surreptitiously turn your Mac into a cryptocurrency miner.
Remember when Apple rather strongly implied that Mac's don't get viruses?
Well, when they tell us applications from the official Mac App Store are 'safe' ...probably wise to take that with a grain of salt too 😬
love these blog posts & tools? you can support them via patreon! Mahalo :)