KextViewr
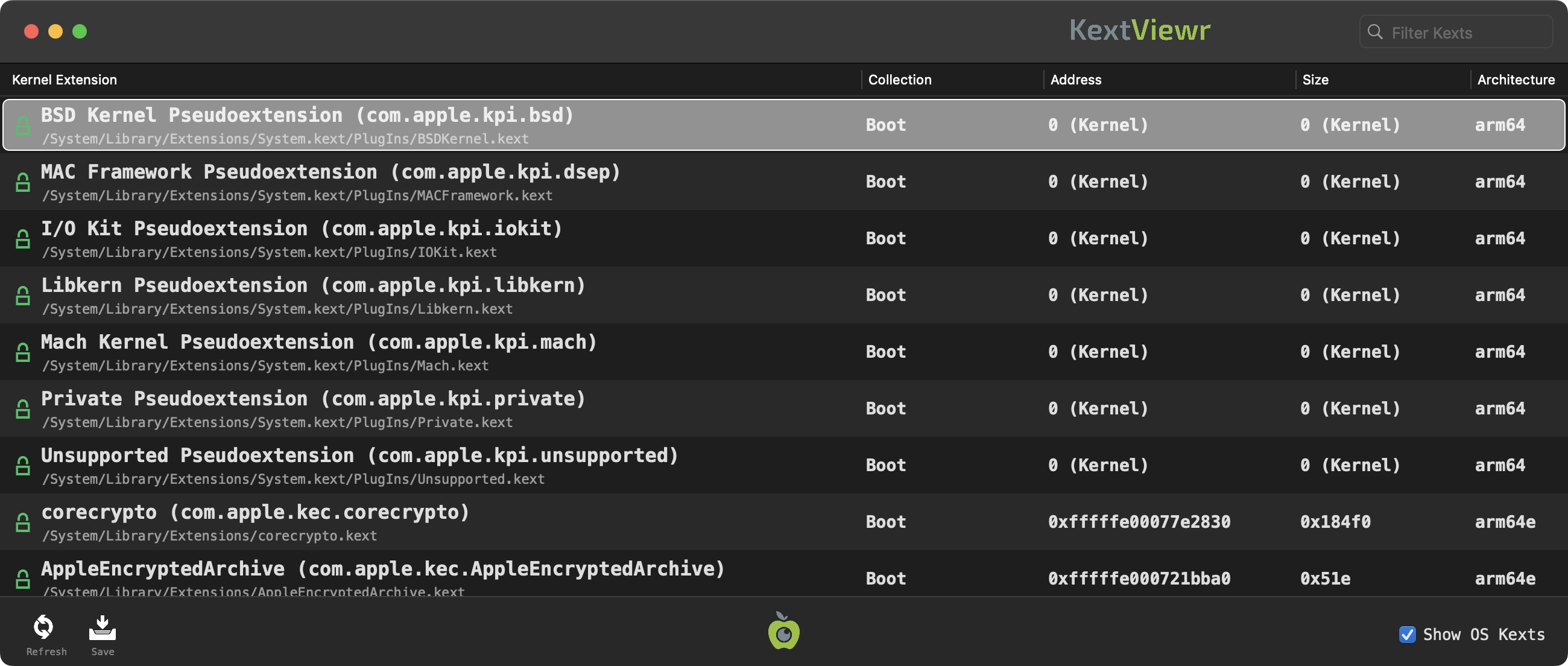
KextViewr is a simple utility that shows you all modules on that are loaded in the OS kernel.
For each loaded kext, it provides information such as their collection (boot, auxiliary, etc.), size, address, and more.
Looking for an older version (compatible with older versions of macOS)?
Older Version: Version 1.1.0.
KextViewr is a utility with a simple goal; display all currently loaded kernel modules (or "kexts"). While Apple's commandline tool 'kmutil' can provide similar information, it's nice to have a UI version, with filter, search, and export capabilities.
To use KextViewr, first download the zip archive containing the application. Depending on your browser, you may need to manually unzip the application by double-clicking on the zipped archive:
To run the application and view all loaded kernel extensions, simply double click on 'KextViewr.app'. KextViewr will query the OS to display all loaded kernel modules. By design, all modules, including those that are part of the OS are displayed. However, the display can be filtered (as described below), to only show 3rd-party modules.
Each row in the table contains a variety of information about a single loaded kernel module. First, an icon indicates whether the module belongs to Apple,
 , or a 3rd-party
, or a 3rd-party  . Following this, the modules' name, bundle id and full path are displayed. These are followed by its collection (boot, system, or auxiliary) address, size, and finally its architecture.
. Following this, the modules' name, bundle id and full path are displayed. These are followed by its collection (boot, system, or auxiliary) address, size, and finally its architecture.
The displayed kernel extensions can be filtered using the 'Filter Kexts' search box, found at the top right corner of the app. Simply begin typing to filter all tasks based on their names, paths, etc. For example, typing 'BSD' will show only modules that contain 'BSD' in their name or path. KextViewr also contains special 'hash-tag' filters that can filter modules based on concepts such as "only system modules" (#apple) or "all non-Apple (3rd-party) modules" (#nonapple). At the bottom of KextViewr's window are several buttons. The first, when clicked will refresh, or reload the list of loaded modules. The second will save the KextViewr's results as JSON. On the right hand-side, unchecking the 'Show OS Kexts' will hide all system Apple-signed kernel modules, leaving only 3rd-party ones visible:

Limitations
As with any security tool, it is important to understand the tool's limitations. In order to get information about loaded kernel extensions, one must possess the com.apple.private.kernel.get-kext-info entitlement. Since it is not possible for 3rd-party applications to obtain this entitlement, KextViewr simply makes use of the OS X utility kmutil, which has the required entitlement:
% codesign --display --entitlements - /usr/bin/kmutil
...
[Key]com.apple.private.kernel.get-kext-info
[Value] [Bool] true
...
[Key]com.apple.private.kernel.get-kext-info
[Value] [Bool] true
Since KextViewr leverages the capabilities of kmutil, if a kernel module is not shown by (or is actively hiding from) kextstat, such a kext will also not be shown by KextViewr. In order words, don't expect KextViewr to reveal the presence of advanced macOS rootkit kernel modules!