TaskExplorer
Explore all the tasks (processes) running on your Mac with TaskExplorer.
Quickly see a task's signature status, loaded dylibs, open files, network connection, and much more!
compatibility: macOS 11+
current version: 2.1.0 (change log)
zip's sha-1: 0F00CCB5C031A3F7F63CC6EF156CBF16BA5C88D0
current version: 2.1.0 (change log)
zip's sha-1: 0F00CCB5C031A3F7F63CC6EF156CBF16BA5C88D0
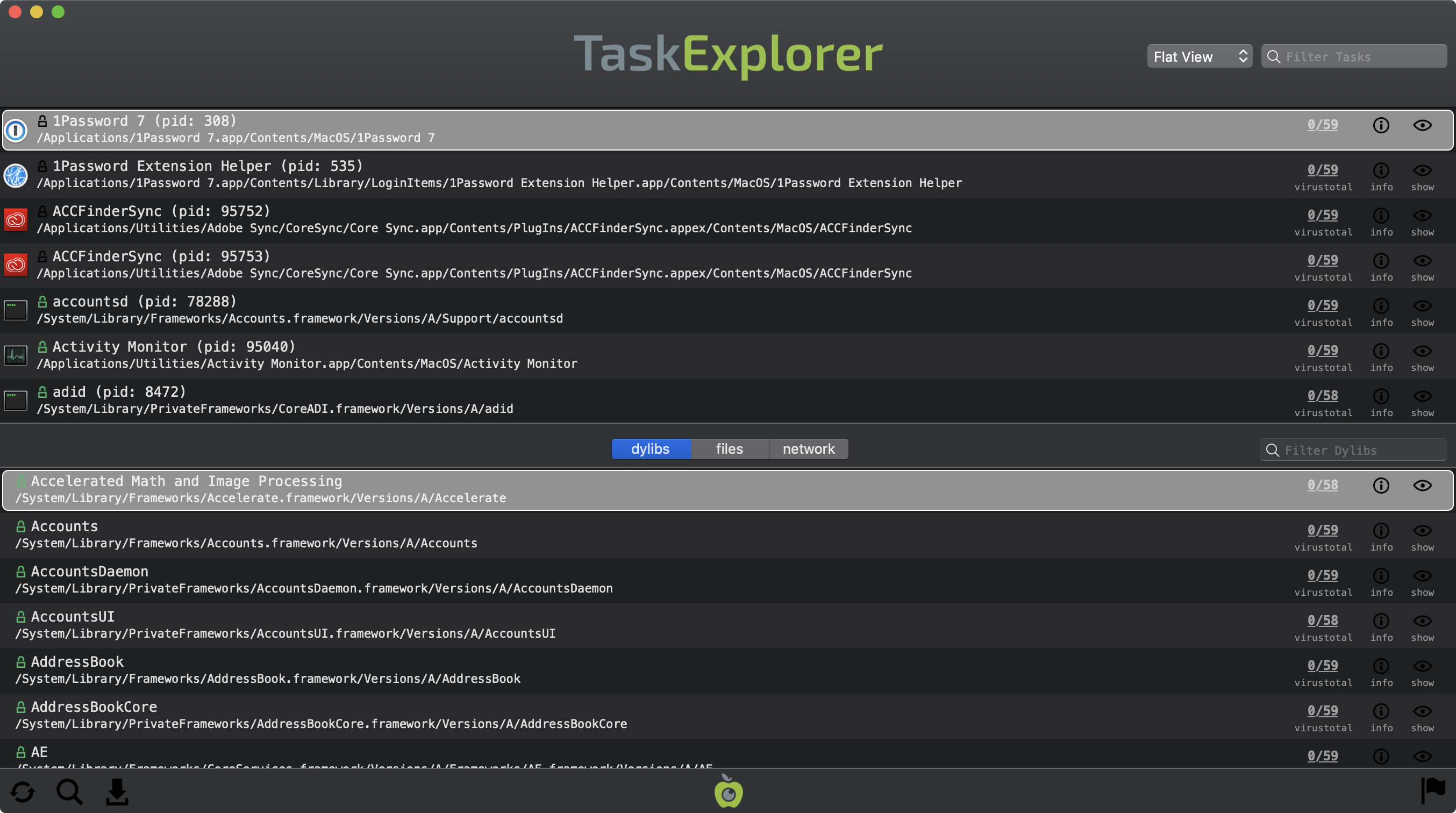
TaskExplorer allows one to visually explore all running processes. Notable features of TaskExplorer include:
- Signing Status
quickly view, (or filter) tasks that are signed by Apple, 3rd-parties, or are unsigned - VirusTotal Integration
detection ratios can reveal known malware, while unknown files can be submitted for analysis - Loaded Dynamic Libraries
for each task, view it's loaded dylibs - Open Files
view all files that a particular task has opened - Network Connections
see the network connection (and its details) created by a task - Global Search
quickly search to find specific items, or unsigned binaries, established network connections, and more!
To run the application and begin exploring tasks, simply double click on 'TaskExplorer.app' The first time TaskExplorer is run, it will display an authorization prompt in order to gain necessary privileges. These privileges are required so that TaskExplorer can enumerate information about remote processes (such as loaded dylibs).
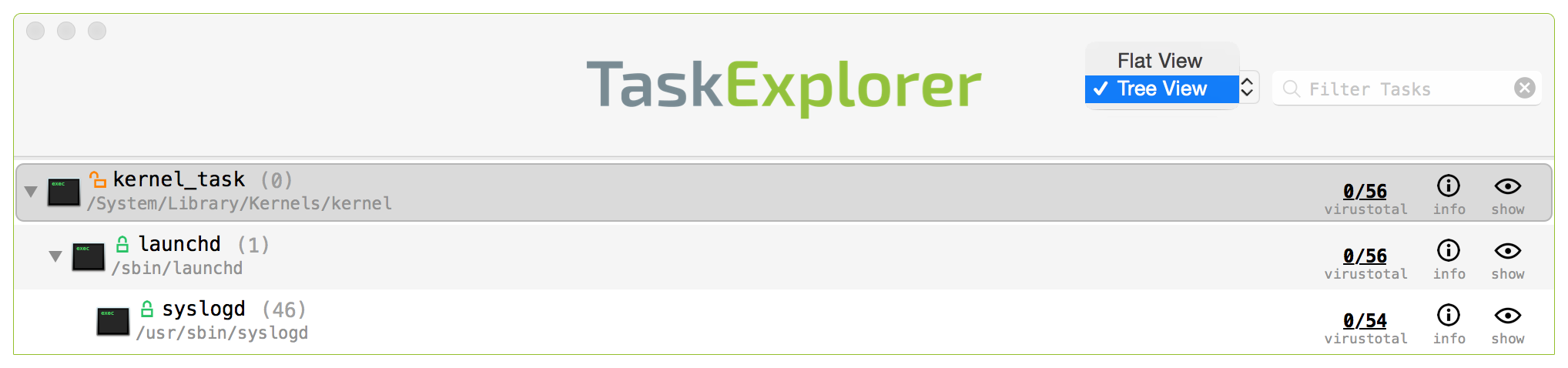
Once authorized, TaskExplorer will begin enumerating all running tasks. The top pane of the application of the displays all running tasks. These tasks can be either be viewed in the default 'Flat View' mode (sorted by name), or in a hierarchical 'Tree View' mode. Use the drop-down selected in the top right corner of the app to toggle between the two views:
Tasks can be filtered using the 'Filter Tasks' search box, found at the top right corner of the app. Simply begin typing to filter all tasks based on their names, paths or pids. For example, typing 'Chrome' will show only tasks that contain 'Chrome' in their name or path. TaskExplorer also contains special 'hash-tag' filters that can filter tasks based on concepts such as 'all non-Apple (3rd-party) tasks' or 'all unsigned tasks' (see the 'Search and Filtering' section below for details).
Each row the top task pane, contains the icon, name, process id (pid), and path of the task. A lock icon next to the task's name, indicates whether the task belongs to Apple,
 , or a 3rd-party (but still signed)
, or a 3rd-party (but still signed)  , or is unsigned
, or is unsigned  . On the right-hand side of each task's row are various informational and actionable buttons. These buttons provide information about item's VirusTotal (anti-virus) scan results, general information about the task, and the ability to view the item in Finder.
. On the right-hand side of each task's row are various informational and actionable buttons. These buttons provide information about item's VirusTotal (anti-virus) scan results, general information about the task, and the ability to view the item in Finder.
Task explorer automatically queries VirusTotal with a hash of the binary in order to retrieve any information. While VirusTotal is being queried, this button displays '■ ■ ■'. Once the query is complete, the title of the button is automatically updated with either the detection ratio, or a '?' if the binary is not known to VirusTotal.
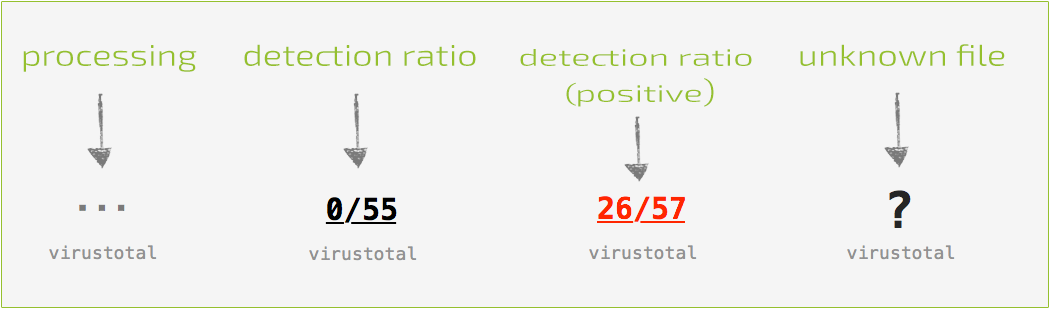
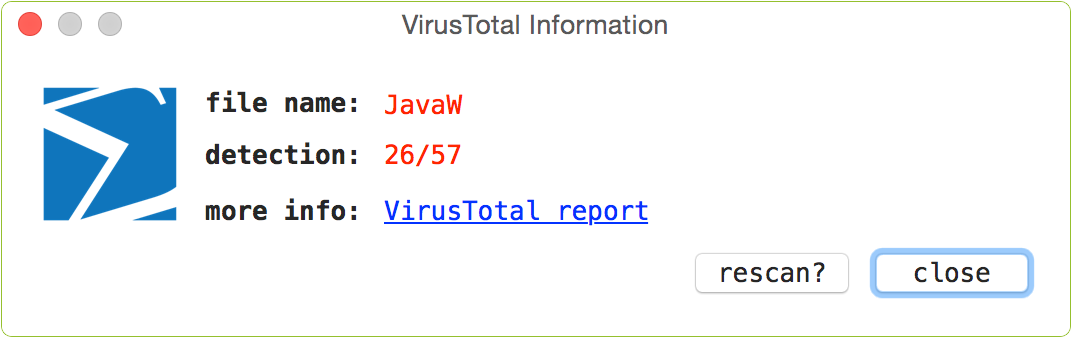
With the query complete, the button can be clicked to reveal a popup containing VirusTotal-specific information about the file. If the file is unknown, clicking the 'submit?' button will submit the file for analysis. Known files contain a link to the full analysis report and a 'rescan?' button that will rescan the file. If known malware is detected, the item's name and VirusTotal button will be highlighted in red.
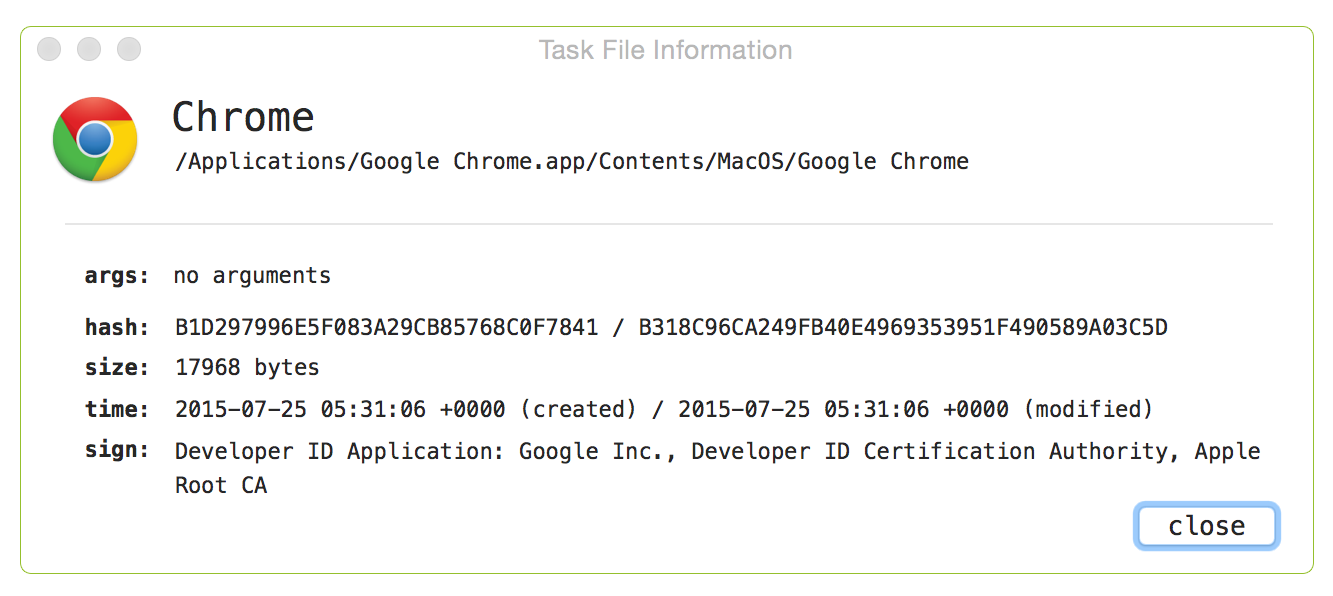
The 'info' button will display detailed information about the task, including its commandline arguments, hashes, and signed status:
Clicking on the final button ('show') in the task's row, will show the task's binary in a Finder window.
The bottom pane can display the selected task's dylibs, open files, or network connections. Simply toggle the segment control to change what is shown. The layout of the items in the bottom pane is fairly similar to the top (tasks') pane. For example, executable binaries will display a VirusTotal detection ratio, and each item (regardless of category), has an 'info' button that can be clicked to display more information about the selected item (dylib, file, or network connection).
Similarly, the items can be filtered by the filter/search box found directory above the lower pane. While any item category (dylib, file, or network connection) can be filtered by simply typing in the field, the certain 'hash-tag' search filters (e.g #nonapple) only apply to executable binaries, and thus are only relevant when the bottom pane is displaying dylibs. The next section, 'Search and Filtering' provides more details on this.
Searching and Filtering
One of the more powerful features of TaskExplorer is its abilty to filter or search for tasks, dylibs, files, and/or network connections. As mentioned, one can search for Tasks via the 'Filter Tasks' search box (top right), as well as for a task's dylibs, files, or network connections via the filter/search box in the middle (right) of the UI above the lower pane. Note that this lower filter box will only search or filter what is currently being displayed in the lower pane. For a global search, click the
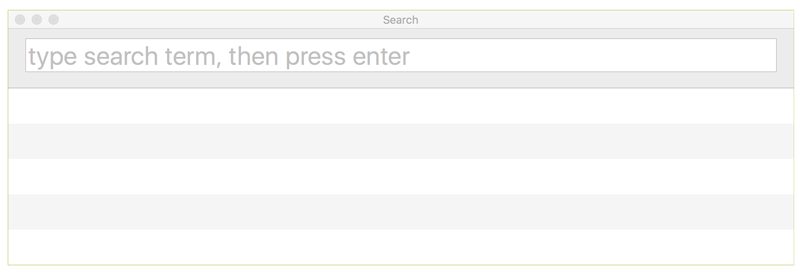
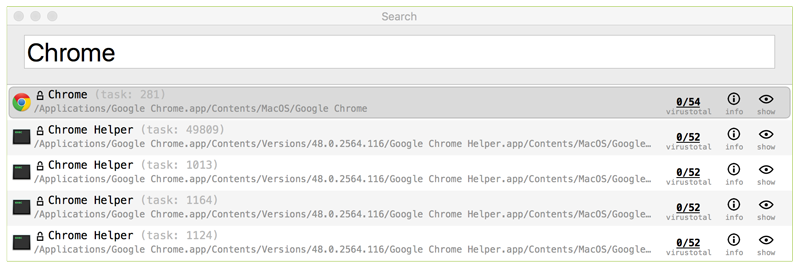
This global search, allows one to search all tasks, dylibs, files, and network connections, all at once! For example typing 'Chrome' (then hitting 'Enter') will show everything that has 'Chrome' in its path, name, etc:
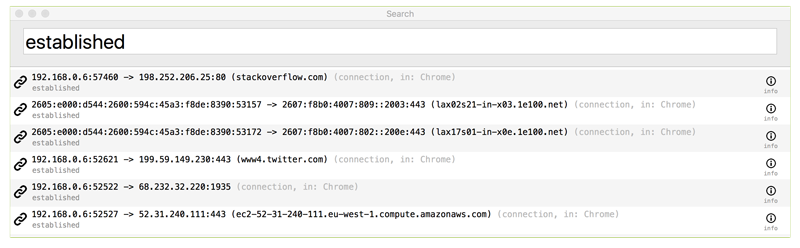
Other examples including typing 'established' to view all connected network connections, or 'listening' to show all listening sockets:
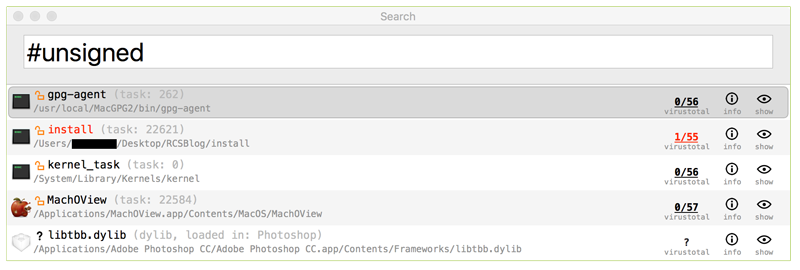
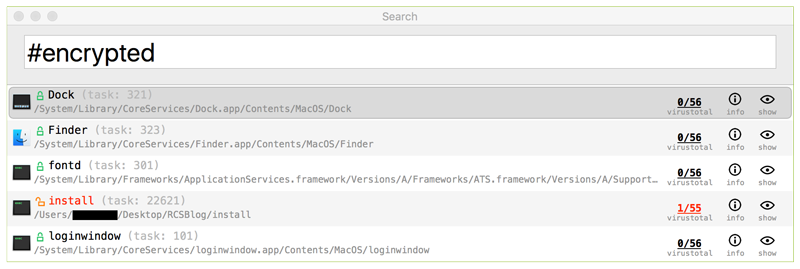
TaskExplorer also contains special 'hash-tag' filters that can filter items (in any filter/search box) based on concepts such as 'all non-Apple (3rd-party) tasks' or 'all unsigned tasks' The list of current support 'hash-tag' filters includes:
- #apple
only display items that belong to the OS (e.g. signed soley by Apple proper) - #nonapple
only display 3rd-party (non-OS) tasks - #signed
only display signed items - #unsigned
only display unsigned items - #flagged
only display items flagged by VirusTotal - #encrypted
only display items flagged that are encrypted (with OSX's native encryption scheme) - #packed
only display items that are packed (note: beta, may list unpacked, but high entropy items) - #notfound
only display items are not found on disk (i.e. binaries that have self-deleted)
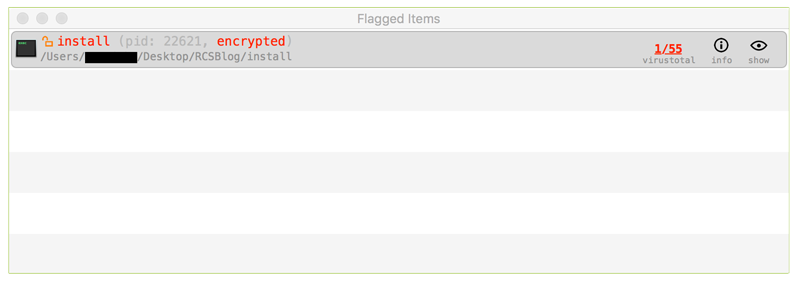
TaskExplorer is integrated with VirusTotal. If any task or dynamic library is flagged (by VirusTotal) as known malware, this will be shown in the 'Flagged Items' pane. To access this pane, click the
Commandline Interface
TaskExplorer (as of version 2.0), can be run via the commandline. There are various benefits to this, including the ability to programmatically enumerate or scan all running tasks and dynamic libraries. Note that TaskExplorer, when run from the commandline, must be executed as root (or via sudo).
Execute the TaskExplorer binary (note: specify the full path to the TaskExplorer binary within its application bundle) with -h or -help to display information about the self-explanatory commandline options:
TASKEXPLORER USAGE: -h or -help display this usage info -scan scan all tasks and dylibs -explore enumerate all tasks and dylibs options: -pretty json output is 'pretty-printed' -pid [pid] just scan/explore the specified task -skipVT do not query VirusTotal (when '-explore' is specified) -detailed for each task; include dylibs, files, & network connections
Note:
To capture the output from TaskExplorer, (as it writes to STDOUT), simply pipe it to a file out of your choice:
$ ./TaskExplorer.app/Contents/MacOS/TaskExplorer -explore > /path/to/some/file.json
To capture the output from TaskExplorer, (as it writes to STDOUT), simply pipe it to a file out of your choice:
$ ./TaskExplorer.app/Contents/MacOS/TaskExplorer -explore > /path/to/some/file.json
FAQs